翻訳は機械翻訳により提供されています。提供された翻訳内容と英語版の間で齟齬、不一致または矛盾がある場合、英語版が優先します。
送信トラフィックの VPC アクセスの有効化
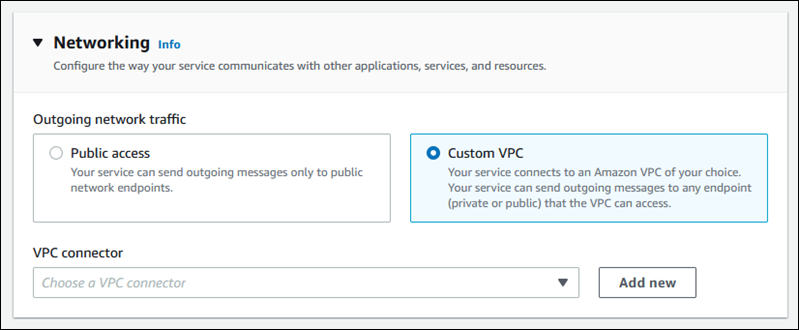
デフォルトでは、 AWS App Runner アプリケーションはパブリックエンドポイントにメッセージを送信できます。これには、独自のソリューション AWS のサービス、およびその他のパブリックウェブサイトまたはウェブサービスが含まれます。アプリケーションは、Amazon Virtual Private Cloud (Amazon VPC) から VPC で実行されるアプリケーションのパブリックエンドポイントにメッセージを送信することもできます。環境の起動時に VPC を設定しない場合、App Runner はパブリックであるデフォルトの VPC を使用します。
カスタム VPC で環境を起動して、送信トラフィックのネットワーク設定とセキュリティ設定をカスタマイズできます。 AWS App Runner サービスが Amazon Virtual Private Cloud (Amazon VPC) からプライベート VPC で実行されるアプリケーションにアクセスできるようにします。これを行うと、アプリケーションは に接続し、Amazon Virtual Private Cloud (Amazon VPC) でホストされている他のアプリケーションにメッセージを送信できます。例としては、Amazon RDS データベース、Amazon ElastiCache、およびプライベート VPC でホストされているその他のプライベートサービスがあります。
VPC コネクタ
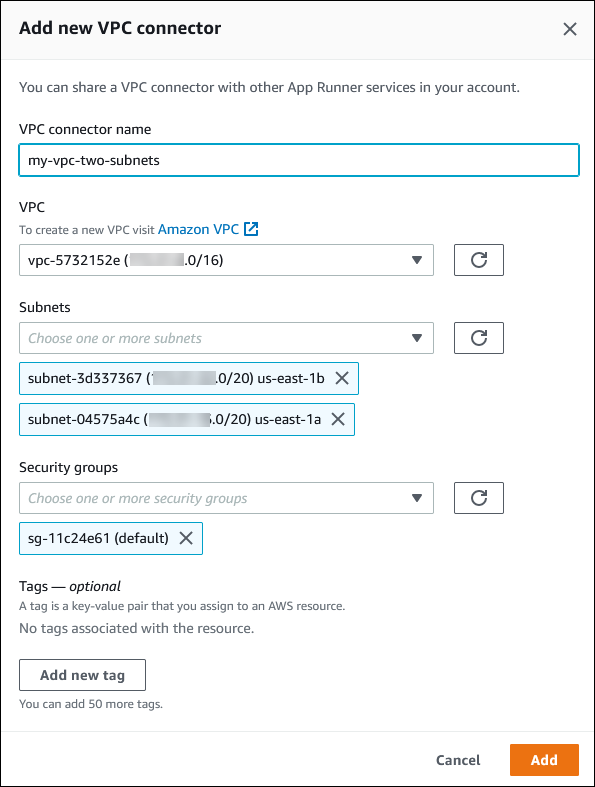
VPC Connector と呼ばれる App Runner コンソールから VPC エンドポイントを作成することで、サービスを VPC に関連付けることができます。VPC コネクタを作成するには、VPC、1 つ以上のサブネット、およびオプションで 1 つ以上のセキュリティグループを指定します。VPC コネクタを設定したら、1 つ以上の App Runner サービスで使用できます。
1 回限りのレイテンシー
アウトバウンドトラフィック用にカスタム VPC コネクタを使用して App Runner サービスを設定すると、1 回限りの起動レイテンシーが 2~5 分になることがあります。スタートアッププロセスは、VPC Connector が他のリソースに接続する準備ができるまで待ってから、サービスステータスを実行中に設定します。サービスを最初に作成するときにカスタム VPC コネクタを使用して設定することも、後でサービスの更新を行って設定することもできます。
同じ VPC コネクタ設定を別のサービスに再利用しても、レイテンシーは発生しないことに注意してください。VPC コネクタの設定は、セキュリティグループとサブネットの組み合わせに基づいています。特定の VPC コネクタ設定では、レイテンシーは VPC Connector Hyperplane ENIs (Elastic Network Interface) の初回作成時に 1 回のみ発生します。
カスタム VPC コネクタと AWS Hyperplane の詳細
App Runner の VPC コネクタは、Network Load Balancer、NAT Gateway、AWS PrivateLink などの複数の AWS リソースの背後にある内部 Amazon ネットワークシステムである AWS Hyperplane に基づいています。 AWS Hyperplane テクノロジーは、高スループットと低レイテンシーの機能に加えて、より高いレベルの共有を提供します。Hyperplane ENI は、VPC コネクタを作成してサービスに関連付けると、サブネットに作成されます。VPC コネクタの設定はセキュリティグループとサブネットの組み合わせに基づいており、複数の App Runner サービスで同じ VPC コネクタを参照できます。その結果、基盤となる Hyperplane ENIs は App Runner サービス間で共有されます。この共有は、リクエストの負荷を処理するために必要なタスクの数をスケールアップしても実行可能であり、VPC 内の IP スペースをより効率的に使用できます。詳細については、AWS コンテナブログの「Deep Dive on AWS App Runner VPC Networking
サブネット
各サブネットは特定のアベイラビリティーゾーンにあります。高可用性を実現するには、少なくとも 3 つのアベイラビリティーゾーンにまたがるサブネットを選択することをお勧めします。リージョンのアベイラビリティーゾーンが 3 つ未満の場合は、サポートされているすべてのアベイラビリティーゾーンでサブネットを選択することをお勧めします。
VPC のサブネットを選択するときは、パブリックサブネットではなくプライベートサブネットを選択するようにしてください。これは、VPC コネクタを作成すると、App Runner サービスが各サブネットに Hyperplane ENI を作成するためです。各 Hyperplane ENI にはプライベート IP アドレスのみが割り当てられ、AWSAppRunnerManaged キーのタグが付けられます。パブリックサブネットを選択すると、App Runner サービスの実行時にエラーが発生します。ただし、サービスがインターネットまたは他のパブリックサービスにアクセスする必要がある場合は AWS のサービス、「」を参照してくださいサブネットを選択する際の考慮事項 。
サブネットを選択する際の考慮事項
-
サービスを VPC に接続すると、アウトバウンドトラフィックはパブリックインターネットにアクセスできません。アプリケーションからのすべてのアウトバウンドトラフィックは、サービスが接続されている VPC を介して送信されます。VPC のすべてのネットワークルールは、アプリケーションのアウトバウンドトラフィックに適用されます。つまり、サービスはパブリックインターネットと AWS APIs にアクセスできません。アクセスするには、次のいずれかを実行します。
-
アクセス AWS のサービス する の VPC エンドポイントを設定します。サービスは、 を使用して Amazon VPC 内に留まります AWS PrivateLink。
-
の一部のアベイラビリティーゾーンは、App Runner サービスで使用できるサブネットをサポート AWS リージョン していません。これらのアベイラビリティーゾーンでサブネットを選択すると、サービスの作成または更新に失敗します。このような状況では、App Runner はサポートされていないサブネットとアベイラビリティーゾーンを指す詳細なエラーメッセージを提供します。これが発生した場合は、サポートされていないサブネットをリクエストから削除してトラブルシューティングを行い、もう一度試してください。
セキュリティグループ
オプションで、指定したサブネット AWS で App Runner がアクセスするために使用するセキュリティグループを指定できます。セキュリティグループを指定しない場合、App Runner は VPC のデフォルトのセキュリティグループを使用します。デフォルトのセキュリティグループでは、すべてのアウトバウンドトラフィックを許可します。
セキュリティグループを追加すると、VCP コネクタにセキュリティレイヤーが追加され、ネットワークトラフィックをより詳細に制御できます。VPC コネクタは、アプリケーションからのアウトバウンド通信にのみ使用されます。アウトバウンドルールを使用して、目的の宛先エンドポイントへの通信を許可します。また、送信先リソースに関連付けられているセキュリティグループに適切なインバウンドルールがあることを確認する必要があります。それ以外の場合、これらのリソースは VPC Connector セキュリティグループからのトラフィックを受け入れることができません。
注記
サービスを VPC に関連付けると、次のトラフィックは影響を受けません。
-
インバウンドトラフィック – アプリケーションが受信する受信メッセージは、関連付けられた VPC の影響を受けません。メッセージは、サービスに関連付けられているパブリックドメイン名を介してルーティングされ、VPC とやり取りしません。
-
App Runner トラフィック – App Runner は、ソースコードとイメージのプル、ログのプッシュ、シークレットの取得など、ユーザーに代わっていくつかのアクションを管理します。これらのアクションが生成するトラフィックは、VPC 経由でルーティングされません。
と Amazon VPC AWS App Runner の統合方法の詳細については、AWS 「App Runner VPC Networking
注記
送信トラフィックの場合、App Runner は現在 IPv4 のみをサポートしています。
VPC アクセスを管理する
注記
サービスのアウトバウンドトラフィック VPC コネクタを作成すると、次のサービス起動プロセスで 1 回限りのレイテンシーが発生します。この設定は、新しいサービスの作成時または作成後にサービスの更新で設定できます。詳細については、このガイド1 回限りのレイテンシーの「Networking with App Runner」の章の「」を参照してください。
次のいずれかの方法を使用して、App Runner サービスの VPC アクセスを管理します。