Bidirectionally integrate AWS Security Hub with Jira software
Joaquin Rinaudo, Amazon Web Services
Summary
This solution supports a bidirectional integration between AWS Security Hub and Jira. Using this solution, you can automatically and manually create and update Jira tickets from Security Hub findings. Security teams can use this integration to notify developer teams of severe security findings that require action.
The solution allows you to:
Select which Security Hub controls automatically create or update tickets in Jira.
In the Security Hub console, use Security Hub custom actions to manually escalate tickets in Jira.
Automatically assign tickets in Jira based on the AWS account tags defined in AWS Organizations. If this tag is not defined, a default assignee is used.
Automatically suppress Security Hub findings that are marked as false positive or accepted risk in Jira.
Automatically close a Jira ticket when its related finding is archived in Security Hub.
Reopen Jira tickets when Security Hub findings reoccur.
Jira workflow
The solution uses a custom Jira workflow that allows developers to manage and document risks. As the issue moves through the workflow, bidirectional integration ensures that the status of the Jira ticket and Security Hub finding is synchronized across the workflows in both services. This workflow is a derivative of SecDevOps Risk Workflow by Dinis Cruz, licensed licensed under Apache License version 2.0
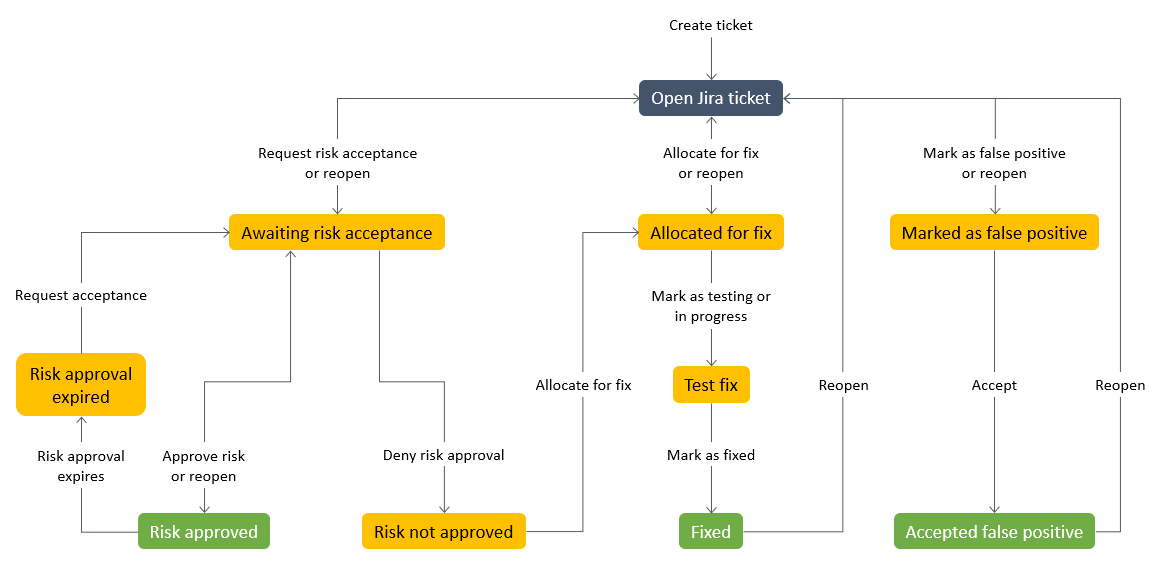
For an example of a Jira ticket automatically generated by this solution, see the Additional information section of this pattern.
Prerequisites and limitations
Prerequisites
If you want to deploy this solution across a multi-account AWS environment:
Your multi-account environment is active and managed by AWS Organizations.
Security Hub is enabled on your AWS accounts.
In AWS Organizations, you have designated a Security Hub administrator account.
You have a cross-account AWS Identity and Access Management (IAM) role that has
AWSOrganizationsReadOnlyAccesspermissions to the AWS Organizations management account.(Optional) You have tagged your AWS accounts with
SecurityContactID. This tag is used to assign Jira tickets to the defined security contacts.
If you want to deploy this solution within a single AWS account:
You have an active AWS account.
Security Hub is enabled on your AWS account.
A Jira Data Center instance
Important
This solution supports use of Jira Cloud. However, Jira Cloud does not support importing XML workflows, so you need to manually re-create the workflow in Jira. You can find of the transitions and status in the GitHub repository.
Administrator permissions in Jira
One of the following Jira tokens:
For Jira Enterprise, a personal access token (PAT). For more information, see Using Personal Access Tokens
(Atlassian support). For Jira Cloud, a Jira API token. For more information, see Manage API tokens
(Atlassian support).
Architecture
This section illustrates the architecture of the solution in various scenarios, such as when the developer and security engineer decide to accept the risk or decide to fix the issue.
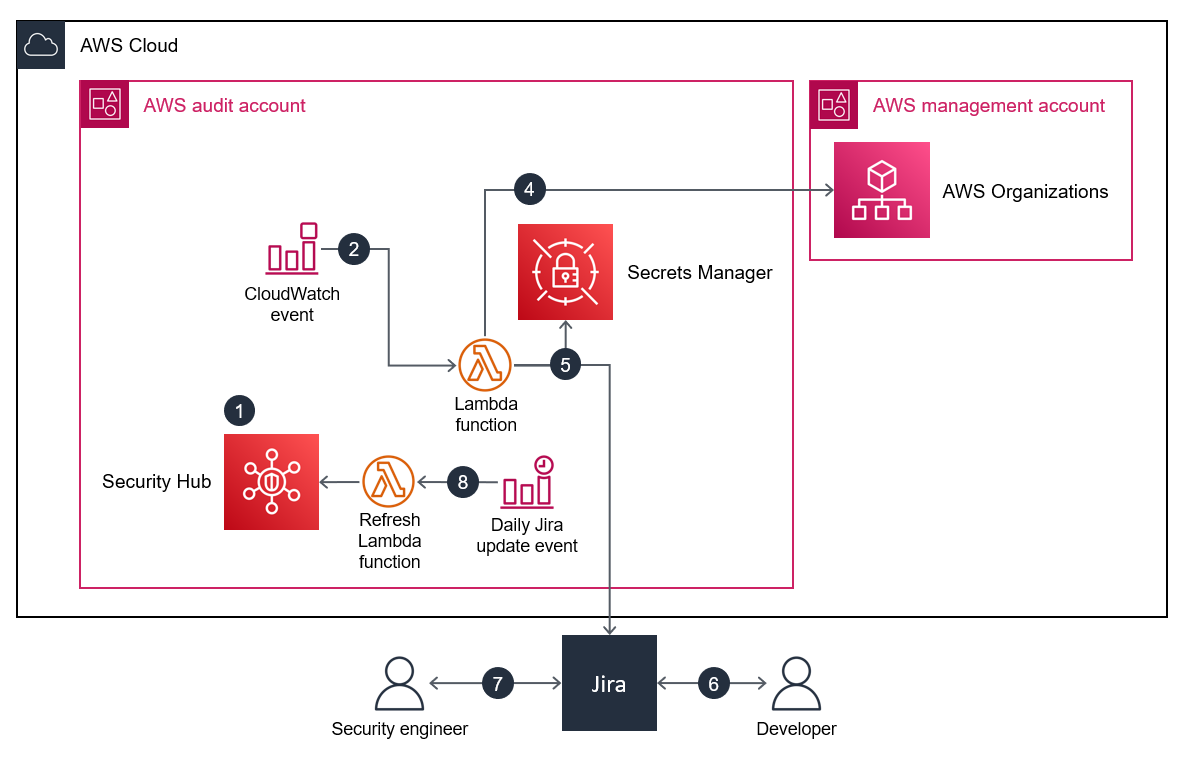
Scenario 1: Developer addresses the issue
Security Hub generates a finding against a specified security control, such as those in the AWS Foundational Security Best Practices standard.
An Amazon CloudWatch event associated with the finding and the
CreateJIRAaction initiates an AWS Lambda function.The Lambda function uses its configuration file and the finding's
GeneratorIdfield to evaluate whether it should escalate the finding.The Lambda function determines the finding should be escalated, it obtains the
SecurityContactIDaccount tag from AWS Organizations in the AWS management account. This ID is associated with the developer and is used as the assignee ID for the Jira ticket.The Lambda function uses the credentials stored in AWS Secrets Manager to create a ticket in Jira. Jira notifies the developer.
The developer addresses the underlying security finding and, in Jira, changes the status of the ticket to
TEST FIX.Security Hub updates the finding as
ARCHIVED, and a new event is generated. This event causes the Lambda function to automatically close the Jira ticket.

Scenario 2: Developer decides to accept the risk
Security Hub generates a finding against a specified security control, such as those in the AWS Foundational Security Best Practices standard.
A CloudWatch event associated with the finding and the
CreateJIRAaction initiates a Lambda function.The Lambda function uses its configuration file and the finding's
GeneratorIdfield to evaluate whether it should escalate the finding.The Lambda function determines the finding should be escalated, it obtains the
SecurityContactIDaccount tag from AWS Organizations in the AWS management account. This ID is associated with the developer and is used as the assignee ID for the Jira ticket.The Lambda function uses the credentials stored in Secrets Manager to create a ticket in Jira. Jira notifies the developer.
The developer decides to accept the risk and, in Jira, changes the status of the ticket to
AWAITING RISK ACCEPTANCE.The security engineer reviews the request and finds the business justification appropriate. The security engineer changes the status of the Jira ticket to
ACCEPTED RISK. This closes the Jira ticket.A CloudWatch daily event initiates the refresh Lambda function, which identifies closed Jira tickets and updates their related Security Hub findings as
SUPPRESSED.
Tools
AWS services
AWS CloudFormation helps you set up AWS resources, provision them quickly and consistently, and manage them throughout their lifecycle across AWS accounts and Regions.
Amazon CloudWatch Events helps you monitor system events for your AWS resources by using rules to match events and route them to functions or streams.
AWS Lambda is a compute service that helps you run code without needing to provision or manage servers. It runs your code only when needed and scales automatically, so you pay only for the compute time that you use.
AWS Organizations is an account management service that helps you consolidate multiple AWS accounts into an organization that you create and centrally manage.
AWS Secrets Manager helps you replace hardcoded credentials in your code, including passwords, with an API call to Secrets Manager to retrieve the secret programmatically.
AWS Security Hub provides a comprehensive view of your security state in AWS. It also helps you check your AWS environment against security industry standards and best practices.
Code repository
The code for this pattern is available on GitHub, in the aws-securityhub-jira-software-integration
Epics
| Task | Description | Skills required |
|---|---|---|
Import the workflow. | As an administrator in Jira, import the Files can be found in the aws-securityhub-jira-software-integration | Jira administrator |
Activate and assign the workflow. | Workflows are inactive until you assign them to a workflow scheme. You then assign the workflow scheme to a project.
| Jira administrator |
| Task | Description | Skills required |
|---|---|---|
Configure the solution parameters. |
| AWS systems administrator |
Identify the findings you want to automate. |
| |
Add the findings to the configuration file. |
The following code example shows automating the
NoteYou can choose to automate different findings for each AWS Region. A good practice to help prevent duplicated findings is to select a single Region to automate creation of controls related to IAM. | AWS systems administrator |
| Task | Description | Skills required |
|---|---|---|
Deploy the integration. | In a command line terminal, enter the following command:
| AWS systems administrator |
Upload Jira credentials to Secrets Manager. |
| AWS systems administrator |
Create the Security Hub custom action. |
| AWS systems administrator |
Related resources
Additional information
Example of a Jira ticket
When a specified Security Hub finding occurs, this solution automatically creates a Jira ticket. The ticket includes the following information:
Title – The title identifies the security issue in the following format:
AWS Security Issue :: <AWS account ID> :: <Security Hub finding title>Description – The description section of the ticket describes the security control associated with the finding, includes a link to the finding in the Security Hub console, and provides a short description of how to handle the security issue in the Jira workflow.
The following is an example of an automatically generated Jira ticket.
Title | AWS Security Issue :: 012345678912 :: Lambda.1 Lambda function policies should prohibit public access. |
|---|---|
Description | What is the problem? We detected a security finding within the AWS account 012345678912 you are responsible for. This control checks whether the AWS Lambda function policy attached to the Lambda resource prohibits public access. If the Lambda function policy allows public access, the control fails. <Link to Security Hub finding> What do I need to do with the ticket?
|