Business Continuity OU
Note
The Business Continuity OU is an advanced use-case topic where your AWS Organization requires data isolation and data residency controls based on unique workloads requirements. In general, most cross account disaster recovery strategies can be implemented through using the Backup account within the Infrastructure OU.
The Business Continuity OU is intended to help teams implement a cross-account disaster recovery strategy. The data is as close to air-gapped as possible and the OU has no workload resources. This creates a secure data bunker to help protect your organization and allow for recovery from severe disasters like ransomware. The secure data bunker should only be accessed when the disaster recovery data for a workload is unavailable, untrustworthy, or destroyed.
The Business Continuity OU does not replace normal disaster recovery plans of your workloads. It’s an additional layer of protection that is meant to enhance the resiliency of your organization. General recommendations for disaster recovery for workloads can be found in Disaster Recovery of Workloads on AWS: Recovery in the Cloud.
For organizations that have data residency requirements and are in a geographical area
that has only a single AWS Region available, using AWS Outposts
Controls
For the Business Continuity OU to be a secure data bunker, access should be heavily restricted to prevent the data from being compromised. Ideally, users with access to the data within the Business Continuity OU should not have access to the regular environment and users with access to the regular environment should not have access to the Business Continuity OU. Apply a combination of SCPs and IAM permissions to this OU and authorized users to ensure that only those AWS services, resources, and actions needed are granted.
Additional consideration
-
Place restrictions on the Backup Administrator role so that backup policies for the Business Continuity OU are not altered.
-
Implement monitoring notifications to confirm that backups have not been interrupted. Refer to the documentation on AWS Backup monitoring.
-
Require all Backup Vaults use AWS Backup Vault Lock in Compliance mode with a minimum retention of 14 days or more.
-
Audit backups regularly to ensure compliance of your backup policies. Refer to the documentation on AWS Backup Audit Manager.
Example structures
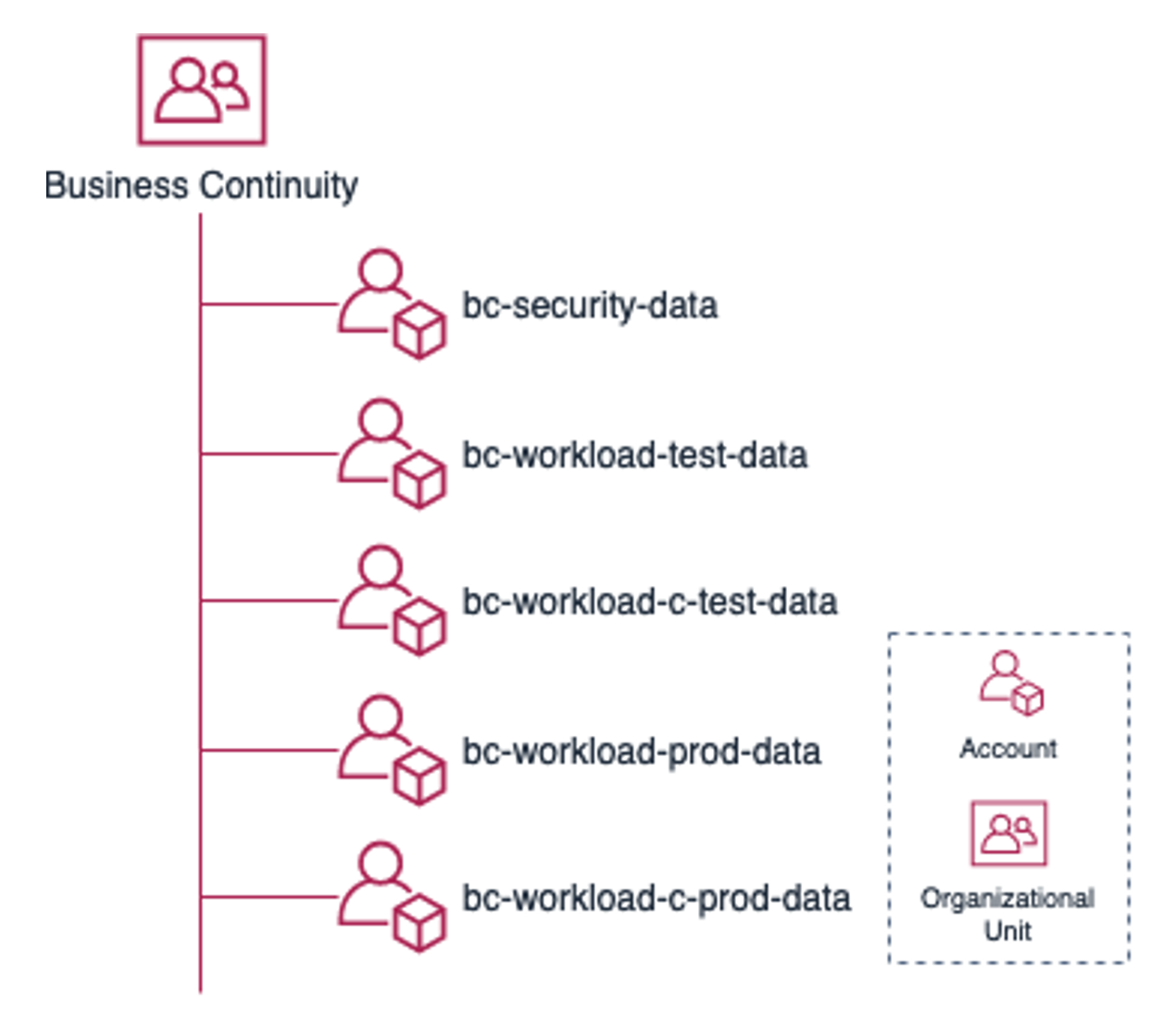
In this example, a company, Rainbows, has a starter AWS environment that follows the production starter organization guidance. Rainbows has three workloads called A, B, and C. They have separate testing and production accounts for each. The data for workloads A and B are non-sensitive and unregulated. However, the data for workload C is highly sensitive and regulated and must be isolated from other workload data.
Following is an example of the Business Continuity OU for the Rainbows company.
Because the data for workloads A and B is non-sensitive and unregulated, you can keep it
in the same business continuity (bc) account, bc-workload-test-data and
bc-workload-prod-data. However, for workload C, the business continuity data is isolated
in separate accounts, bc-workload-c-test-data and bc-workload-c-prod-data, because the
workload is highly sensitive and regulated.
Note
Some companies choose to keep each workload’s data separated in individual accounts for an enhanced security posture, regardless of a regulatory or compliance need.
Business Continuity OU example structure