Ensure AWS load balancers use secure listener protocols (HTTPS, SSL/TLS)
Chandini Penmetsa and Purushotham G K, Amazon Web Services
Summary
On the Amazon Web Services (AWS) Cloud, Elastic Load Balancing automatically distributes incoming application traffic across multiple targets, such as Amazon Elastic Compute Cloud (Amazon EC2) instances, containers, IP addresses, and AWS Lambda functions. The load balancers use listeners to define the ports and protocols that the load balancer uses to accept traffic from users. Application Load Balancers make routing decisions at the application layer and use the HTTP/HTTPS protocols. Network Load Balancers make routing decisions at the transport layer and use the Transmission Control Protocol (TCP), Transport Layer Security (TLS), User Datagram Protcol (UDP), or TCP_UDP protocols. Classic Load Balancers make routing decisions at either the transport layer, using TCP or Secure Sockets Layer (SSL) protocols, or at the application layer, using HTTP/HTTPS.
Your organization might have a security or compliance requirement that load balancers accept traffic from users only on secure protocols, such as HTTPS or SSL/TLS.
This pattern provides a security control that uses an Amazon EventBridge rule to monitor the CreateListener and ModifyListener API calls for Application Load Balancers and Network Load Balancers, and the CreateLoadBalancerListeners and CreateLoadBalancer API calls for Classic Load Balancers. If HTTP, TCP/UDP, or TCP_UDP is used for the load balancer's listener protocol, the control invokes a Lambda function. The Lambda function publishes a message to an Amazon Simple Notification Service (Amazon SNS) topic to send a notification that contains the load balancer details.
Prerequisites and limitations
Prerequisites
An active AWS account
An email address where you want to receive the violation notification
An Amazon Simple Storage Service (Amazon S3) bucket to store the Lambda code .zip file
Limitations
This security control does not check for existing load balancers unless an update is made to the load balancer listeners.
This security control is regional and must be deployed in the AWS Regions that you intend to monitor.
Architecture
Target technology stack
Lambda function
Amazon SNS topic
EventBridge rule
Target architecture
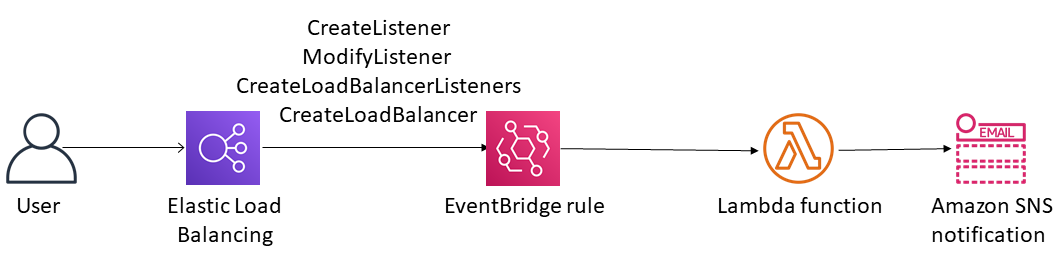
Automation and scale
If you are using AWS Organizations, you can use AWS Cloudformation StackSets to deploy this template in multiple accounts that you want this to monitor.
Tools
AWS CloudFormation – AWS CloudFormation is a service that helps you model and set up AWS resources by using infrastructure as code.
Amazon EventBridge – Amazon EventBridge delivers a stream of real-time data from your own applications, software as a service (SaaS) applications, and AWS services, routing that data to targets such as Lambda functions.
AWS Lambda – Lambda supports running code without provisioning or managing servers.
Amazon S3 – Amazon Simple Storage Service (Amazon S3) is a highly scalable object storage service that can be used for a wide range of storage solutions, including websites, mobile applications, backups, and data lakes.
Amazon SNS – Amazon Simple Notification Service (Amazon SNS) coordinates and manages the delivery or sending of messages between publishers and clients, including web servers and email addresses. Subscribers receive all messages published to the topics to which they subscribe, and all subscribers to a topic receive the same messages.
Best practices
Ensure that the SNS topic used isn’t publicly accessible. For more information, see the AWS documentation.
Epics
| Task | Description | Skills required |
|---|---|---|
Define the S3 bucket. | On the Amazon S3 console, choose or create an S3 bucket with a unique name that does not contain leading slashes. An S3 bucket name is globally unique, and the namespace is shared by all AWS accounts. Your S3 bucket needs to be in the same Region as the load balancer that is being evaluated. | Cloud Architect |
Upload the Lambda code to the S3 bucket. | Upload the Lambda code .zip file that's provided in the "Attachments" section to the defined S3 bucket. | Cloud Architect |
Deploy the AWS CloudFormation template. | On the AWS CloudFormation console, in the same AWS Region as the S3 bucket, deploy the template that is provided in the "Attachments" section. In the next epic, provide the values for the parameters. | Cloud Architect |
| Task | Description | Skills required |
|---|---|---|
Name the S3 bucket. | Enter the name of the S3 bucket that you created in the first epic. | Cloud Architect |
Provide the Amazon S3 prefix. | Provide the location of the Lambda code .zip file in your S3 bucket, without leading slashes (for example, | Cloud Architect |
Provide the SNS topic ARN. | Provide the SNS topic Amazon Resource Name (ARN) if you want to use an existing SNS topic for violation notifications. To create a new SNS topic, keep the value as | Cloud Architect |
Provide an email address. | Provide an active email address to receive Amazon SNS notifications. | Cloud Architect |
Define the logging level. | Define the logging level and frequency for your Lambda function. | Cloud Architect |
| Task | Description | Skills required |
|---|---|---|
Download the template. | Download the CloudFormation template that's provided in the Attachments section. | Cloud architect |
Create the stack. | In the same Region as the S3 bucket, navigate to the CloudFormation service console, and deploy the downloaded template. Refer to the previous epic for parameter details. | Cloud architect |
Verify the resources. | After the stack is created completely, navigate to the Resources tab, and verify the resources. The template will create the following resources:
| Cloud architect |
| Task | Description | Skills required |
|---|---|---|
Confirm the subscription. | When the template successfully deploys, if a new SNS topic was created, a subscription email message is sent to the email address provided in the parameters. You must confirm this email subscription to receive violation notifications. | Cloud architect |
Troubleshooting
| Issue | Solution |
|---|---|
Stack creation failed. Error occurred while GetObject. S3 Error Code: PermanentRedirect. S3 Error Message: The bucket is in this region: xx-xxxx-1. Please use this region to retry the request. | Make sure that the S3 bucket Region and the Region where the stack is being deployed are the same. |
Stack creation failed. The runtime parameter of python3.6 is no longer supported for creating or updating AWS Lambda functions. | Update the downloaded template at line 186 from Python version 3.6 to 3.9. |
Related resources
Attachments
To access additional content that is associated with this document, unzip the following file: attachment.zip