Help enforce DynamoDB tagging
Created by Mansi Suratwala (AWS)
Environment: Production | Technologies: Databases; CloudNative; Security, identity, compliance | Workload: All other workloads |
AWS services: Amazon CloudWatch; Amazon DynamoDB; AWS Lambda; Amazon SNS |
Summary
This pattern sets up automatic notifications when a predefined Amazon DynamoDB tag is missing or removed from a DynamoDB resource on the Amazon Web Services (AWS) Cloud.
DynamoDB is a fully managed NoSQL database service that provides fast and predictable performance with scalability. DynamoDB lets you offload the administrative burdens of operating and scaling a distributed database. When you use DynamoDB, you don't have to worry about hardware provisioning, setup and configuration, replication, software patching, or cluster scaling.
The pattern uses an AWS CloudFormation template, which creates an Amazon CloudWatch Events event and an AWS Lambda function. The event watches for any new or existing DynamoDB tagging information by using AWS CloudTrail. If a predefined tag is missing or removed, CloudWatch triggers a Lambda function, which sends you an Amazon Simple Notification Service (Amazon SNS) notification informing you of the violation.
Prerequisites and limitations
Prerequisites
An active AWS account
An Amazon Simple Storage Service (Amazon S3) bucket for the Lambda .zip file that contains the Python script for running the Lambda function
Limitations
The solution works only when the
TagResourceorUntagResourceCloudTrail events occur. It does not create notifications for any other events.
Architecture
Target technology stack
Amazon DynamoDB
AWS CloudTrail
Amazon CloudWatch
AWS Lambda
Amazon S3
Amazon SNS
Target architecture
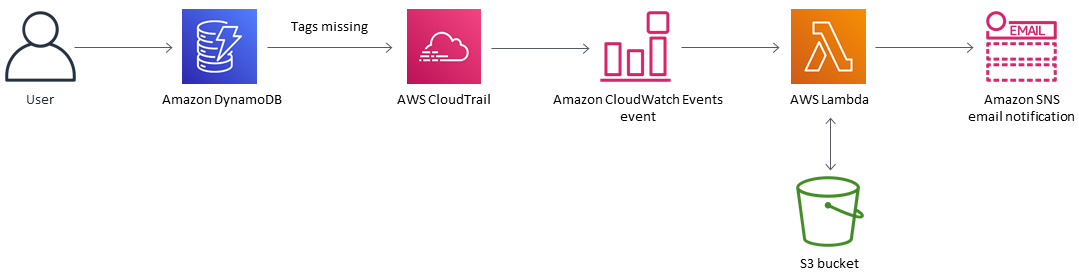
Automation and scale
You can use the AWS CloudFormation template multiple times for different AWS Regions and accounts. You need to run the template only once in each Region or account.
Tools
Tools
Amazon DynamoDB – DynamoDB is a fully managed NoSQL database service that provides fast and predictable performance with scalability.
AWS CloudTrail – CloudTrail is an AWS service that helps you with governance, compliance, and operational and risk auditing of your AWS account. Actions taken by a user, role, or an AWS service are recorded as events in CloudTrail.
Amazon CloudWatch Events – Amazon CloudWatch Events delivers a near-real time stream of system events that describe changes in AWS resources.
AWS Lambda – Lambda is a compute service that supports running code without needing to provision or manage servers. Lambda runs your code only when needed and scales automatically, from a few requests per day to thousands per second.
Amazon S3 – Amazon Simple Storage Service (Amazon S3) is a highly scalable object storage service that can be used for a wide range of storage solutions, including websites, mobile applications, backups, and data lakes.
Amazon SNS – Amazon Simple Notification Service (Amazon SNS) is a web service that enables applications, end-users, and devices to instantly send and receive notifications from the cloud.
Code
A .zip file of the project is available as an attachment.
Epics
| Task | Description | Skills required |
|---|---|---|
Define the S3 bucket. | On the Amazon S3 console, choose or create an S3 bucket with a unique name that does not contain leading slashes. This S3 bucket will host the Lambda code .zip file. Your S3 bucket must be in the same AWS Region as the DynamoDB resource that is being monitored. | Cloud Architect |
| Task | Description | Skills required |
|---|---|---|
Upload the Lambda code to the S3 bucket. | Upload the Lambda code .zip file provided in the Attachments section to the S3 bucket. The S3 bucket must be in the same Region as the DynamoDB resource that is being monitored. | Cloud Architect |
| Task | Description | Skills required |
|---|---|---|
Deploy the AWS CloudFormation template. | On the AWS CloudFormation console, deploy the AWS CloudFormation template that's provided in the Attachments section. In the next epic, provide values for the parameters. | Cloud Architect |
| Task | Description | Skills required |
|---|---|---|
Name the S3 bucket. | Enter the name of the S3 bucket that you created or chose in the first epic. | Cloud Architect |
Provide the Amazon S3 key. | Provide the location of the Lambda code .zip file in your S3 bucket, without leading slashes (for example, | Cloud Architect |
Provide an email address | Provide an active email address to receive Amazon SNS notifications. | Cloud Architect |
Define the logging level. | Define the logging level and frequency for your Lambda function. | Cloud Architect |
Enter the required DynamoDB tag keys. | Be sure that the tags are separated by commas, with no spaces between them (for example, | Cloud Architect |
| Task | Description | Skills required |
|---|---|---|
Confirm the subscription. | When the template successfully deploys, it sends a subscription email to the email address that you provided. To receive violation notifications, you must confirm this email subscription. | Cloud Architect |
Related resources
Attachments
To access additional content that is associated with this document, unzip the following file: attachment.zip