Monitor EC2 instance key pairs using AWS Config
Wassim Benhallam, Sergio Bilbao Lopez, and Vikrant Telkar, Amazon Web Services
Summary
When launching an Amazon Elastic Compute Cloud (Amazon EC2) instance on the Amazon Web Services (AWS) Cloud, a best practice is to create or use an existing key pair to connect to the instance. The key pair, which consists of a public key stored in the instance and a private key provided to the user, allows secure access through Secure Shell (SSH) to the instance and avoids the use of passwords. However, users can sometimes inadvertently launch instances without attaching a key pair. Because key pairs can be assigned only during the launch of an instance, it's important to quickly identify and flag as noncompliant any instances launched without key pairs. This is particularly useful when working in accounts or environments that mandate the use of key pairs for instance access.
This pattern describes how to create a custom rule in AWS Config to monitor EC2 instance key pairs. When instances are identified as noncompliant, an alert is sent using Amazon Simple Notification Service (Amazon SNS) notifications initiated through an Amazon EventBridge event.
Prerequisites and limitations
Prerequisites
An active AWS account
AWS Config enabled for the AWS Region you want to monitor and configured to record all AWS resources
Limitations
This solution is Region-specific. All resources should be created in the same AWS Region.
Architecture
Target technology stack
AWS Config
Amazon EventBridge
AWS Lambda
Amazon SNS
Target architecture
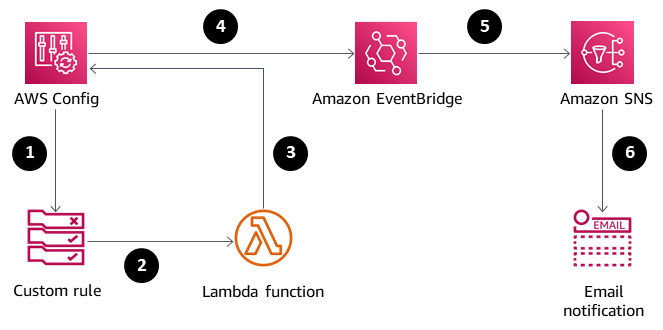
AWS Config initiates the rule.
The rule invokes the Lambda function to evaluate compliance of EC2 instances.
The Lambda function sends the updated compliance state to AWS Config.
AWS Config sends an event to EventBridge.
EventBridge publishes compliance change notifications to an SNS topic.
Amazon SNS sends an alert in email.
Automation and scale
The solution can monitor any number of EC2 instances within a Region.
Tools
Tools
AWS Config – AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. AWS Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations.
Amazon EventBridge – Amazon EventBridge is a serverless event bus service for connecting your applications with data from a variety of sources.
AWS Lambda – AWS Lambda is a serverless compute service that supports running code without provisioning or managing servers, creating workload-aware cluster scaling logic, maintaining event integrations, or managing runtimes.
Amazon SNS – Amazon Simple Notification Service (Amazon SNS) is a fully managed messaging service for both application-to-application (A2A) and application-to-person (A2P) communication.
Code
The code for the Lambda function is attached.
Epics
| Task | Description | Skills required |
|---|---|---|
| Create an AWS Identity and Access Management (IAM) role for Lambda. | On the AWS Management Console, choose IAM, and then create the role, using Lambda as the trusted entity and adding the | DevOps |
| Create and deploy the Lambda function. |
| DevOps |
| Task | Description | Skills required |
|---|---|---|
| Add a custom AWS Config rule. | On the AWS Config console, add a custom rule, using the following settings:
For more information, see the AWS documentation. | DevOps |
| Task | Description | Skills required |
|---|---|---|
| Create the SNS topic and subscription. | On the Amazon SNS console, create a topic using Standard as the type, and then create a subscription using Email as the protocol. When you receive the confirmation email message, choose the link to confirm the subscription. For more information, see the AWS documentation. | DevOps |
| Create an EventBridge rule to initiate Amazon SNS notifications. | On the EventBridge console, create a rule, using the following settings:
For more information, see the AWS documentation. | DevOps |
| Task | Description | Skills required |
|---|---|---|
| Create EC2 instances. | Create two EC2 instances of any type and attach a key pair, and create one EC2 instance without a key pair. | DevOps |
| Verify the rule. |
| DevOps |
Related resources
Attachments
To access additional content that is associated with this document, unzip the following file: attachment.zip