Send a notification when an IAM user is created
Mansi Suratwala and Sergiy Shevchenko, Amazon Web Services
Summary
On Amazon Web Services (AWS), you can use this pattern to deploy an AWS CloudFormation template to receive notifications automatically when AWS Identity and Access Management (IAM) users are created.
Using IAM, you can manage access to AWS services and resources securely. You can create and manage AWS users and groups, and use permissions to allow and deny those users and groups access to AWS resources.
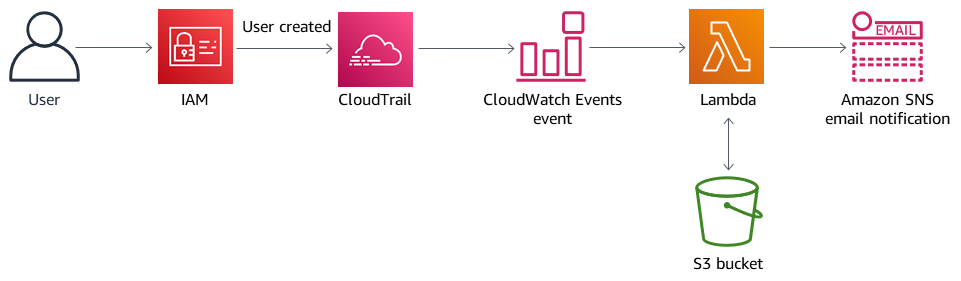
The CloudFormation template creates an Amazon CloudWatch Events event and an AWS Lambda function. The event uses AWS CloudTrail to monitor for any IAM user being created in the AWS account. If a user is created, the CloudWatch Events event initiates a Lambda function, which sends you an Amazon Simple Notification Service (Amazon SNS) notification informing you of the new user creation event.
Prerequisites and limitations
Prerequisites
An active AWS account
An AWS CloudTrail trail created and deployed
Limitations
The AWS CloudFormation template must be deployed for
CreateUseronly.
Architecture
Target technology stack
IAM
AWS CloudTrail
Amazon CloudWatch Events
AWS Lambda
Amazon Simple Storage Service (Amazon S3)
Amazon SNS
Target architecture
Automation and scale
You can use the AWS CloudFormation template multiple times for different AWS Regions and accounts. You need to run it only once in each Region or account. To automate deployment to multiple accounts, use AWS CloudFormation StackSets. The CloudFormation template will be able to deploy all the required resources in each account.
Tools
Tools
IAM – AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
AWS CloudFormation – AWS CloudFormation helps you model and set up your Amazon Web Services resources so that you can spend less time managing those resources and more time focusing on your applications that run in AWS. You create a template that describes all the AWS resources that you want, and CloudFormation takes care of provisioning and configuring those resources for you.
AWS CloudTrail – AWS CloudTrail helps you manage governance, compliance, and operational and risk auditing of your AWS account. Actions taken by a user, a role, or an AWS service are recorded as events in CloudTrail. Events include actions taken in the AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs.
Amazon CloudWatch Events – Amazon CloudWatch Events delivers a near-real-time stream of system events that describe changes in AWS resources.
AWS Lambda – AWS Lambda is a compute service that supports running code without provisioning or managing servers. Lambda runs your code only when needed and scales automatically, from a few requests per day to thousands per second.
Amazon S3 – Amazon Simple Storage Service (Amazon S3) is storage for the internet. You can use Amazon S3 to store and retrieve any amount of data at any time, from anywhere on the web.
Amazon SNS – Amazon Simple Notification Service (Amazon SNS) is a managed service that provides message delivery using Lambda, HTTP, email, mobile push notifications, and mobile text messages (SMS).
Code
A .zip file of the project is available as an attachment.
Epics
| Task | Description | Skills required |
|---|---|---|
Define the S3 bucket. | Open the Amazon S3 console, and choose or create an S3 bucket. This S3 bucket will host the Lambda code .zip file. The S3 bucket name cannot contain leading slashes. | Cloud architect |
| Task | Description | Skills required |
|---|---|---|
Upload the Lambda code. | Upload the Lambda code .zip file provided in the Attachments section to the S3 bucket that you defined. | Cloud architect |
| Task | Description | Skills required |
|---|---|---|
Deploy the CloudFormation template. | On the CloudFormation console, deploy the CloudFormation | Cloud architect |
| Task | Description | Skills required |
|---|---|---|
Provide the S3 bucket name. | Enter the name of the S3 bucket that you created or chose in the first epic. | Cloud architect |
Provide the S3 key. | Provide the location of the Lambda code .zip file in your S3 bucket, without leading slashes (for example, | Cloud architect |
Provide an email address. | Provide an active email address to receive Amazon SNS notifications. | Cloud architect |
Define the logging level. | Define the logging level and frequency for your Lambda function. | Cloud architect |
| Task | Description | Skills required |
|---|---|---|
Confirm the subscription. | When the template successfully deploys, it sends a subscription email message to the email address provided. To receive notifications, you must confirm this email subscription. | Cloud architect |
Related resources
Attachments
To access additional content that is associated with this document, unzip the following file: attachment.zip