AWS Key Management Service
AWS Key Management Service (AWS KMS) is an AWS service that makes it easy for you to create and control the
encryption keys that are used to encrypt your data. The AWS KMS keys that you create in AWS KMS
are protected by FIPS 140-2 validated cryptographic modules
Many AWS services are integrated with AWS KMS so they encrypt your data with KMS keys in your AWS account. AWS KMS is also integrated with AWS CloudTrail to deliver detailed logs of all cryptographic operations that use your KMS keys and management operations that change their configuration. This detailed logging helps you fulfill your auditing, regulatory and compliance requirements.
Why use AWS KMS?
AWS KMS protects the KMS keys that protect your data.
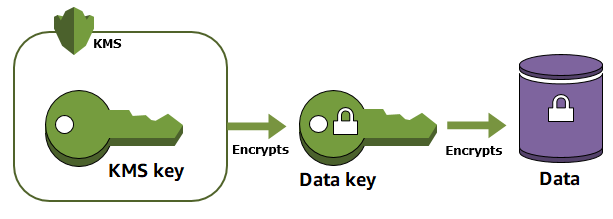
In the classic scenario, you encrypt your data using data key A. But you need to protect data key A, so you encrypt data key A by using data key B. Now data key B is vulnerable, so you encrypt it by using data key C. And, so on. This encryption technique, which is called envelope encryption, always leaves one last encryption key unencrypted so you can decrypt your encryption keys and data. That last unencrypted (or plaintext) key is called a root key.

AWS KMS protects your root keys. KMS keys are created, managed, used, and deleted entirely within AWS KMS . They never leave the service unencrypted. To use or manage your KMS keys, you call AWS KMS .
Using and managing KMS keys
Symmetric KMS keys are 256-bit Advanced Encryption Standard (AES) keys that are not exportable. They spend their entire lifecycle entirely within AWS KMS.
You can also create asymmetric RSA or elliptic curve (ECC) KMS keys backed by asymmetric key pairs. The public key in each asymmetric KMS key is exportable, but the private key remains within AWS KMS.
You can create, view, and manage the KMS keys in your AWS account from the AWS Management Console and AWS KMS API operations. You have full control over your customer managed KMS keys.
You can:
-
Establish policies that determine who can use and manage your KMS keys.
-
Enable and disable your KMS keys.
-
Enable and disable automatic rotation of the key material in your KMS keys.
-
Schedule deletion of your KMS keys when you are finished using them.
You can also use your KMS keys in cryptographic operations. You can encrypt and decrypt small amounts of data directly under the KMS keys. But KMS keys are typically used to generate, encrypt, decrypt, and reencrypt exportable data keys that protect your data outside of AWS KMS. You can also give other AWS services permission to use your KMS keys on your behalf to encrypt the data that the service stores and manages for you.
More resources and information
You can read about AWS Key Management Service in the AWS Key Management Service Developer Guide and
the AWS Key Management Service API Reference. If you have questions, read and post
on the AWS KMS Discussion
Forum
If you are required to control and manage the hardware security modules that generate and store your encryption keys, learn about AWS CloudHSM.
If you need help using encryption keys to encrypt your data, such as the data keys that AWS KMS returns, learn about the AWS Encryption SDK.