Terjemahan disediakan oleh mesin penerjemah. Jika konten terjemahan yang diberikan bertentangan dengan versi bahasa Inggris aslinya, utamakan versi bahasa Inggris.
Buat jaringan VPC
Alur Kerja Terkelola Amazon untuk Apache Airflow memerlukan VPC Amazon dan komponen jaringan tertentu untuk mendukung lingkungan. Panduan ini menjelaskan berbagai opsi untuk membuat jaringan VPC Amazon untuk lingkungan Alur Kerja Terkelola Amazon untuk Apache Airflow.
catatan
Apache Airflow bekerja paling baik di lingkungan jaringan latensi rendah. Jika Anda menggunakan VPC Amazon yang sudah ada yang merutekan lalu lintas ke wilayah lain atau ke lingkungan lokal, sebaiknya tambahkan titik akhir AWS PrivateLink untuk Amazon SQS, Amazon S3, dan. CloudWatch AWS KMS Untuk informasi selengkapnya tentang mengonfigurasi AWS PrivateLink Amazon MWAA, lihat Membuat jaringan VPC Amazon tanpa akses internet.
Daftar Isi
Prasyarat
The AWS Command Line Interface (AWS CLI) adalah alat open source yang memungkinkan Anda berinteraksi dengan AWS layanan menggunakan perintah di shell baris perintah Anda. Untuk menyelesaikan langkah-langkah di halaman ini, Anda memerlukan yang berikut:
Sebelum Anda mulai
-
Jaringan VPC yang Anda tentukan untuk lingkungan Anda tidak dapat diubah setelah lingkungan dibuat.
-
Anda dapat menggunakan perutean pribadi atau publik untuk server Web VPC Amazon dan Apache Airflow. Untuk melihat daftar opsi, lihatContoh kasus penggunaan untuk VPC Amazon dan mode akses Apache Airflow.
Opsi untuk membuat jaringan VPC Amazon
Bagian berikut menjelaskan opsi yang tersedia untuk membuat jaringan VPC Amazon untuk suatu lingkungan.
catatan
Amazon MWAA tidak mendukung penggunaan use1-az3 Availability Zone (AZ) di Wilayah AS Timur (Virginia N.). Saat membuat VPC untuk Amazon MWAA di wilayah AS Timur (Virginia N.), Anda harus secara eksplisit menetapkan templat in (CFN). AvailabilityZone AWS CloudFormation Nama zona ketersediaan yang ditetapkan tidak boleh dipetakan. use1-az3 Anda dapat mengambil pemetaan rinci nama AZ ke AZ yang sesuai IDs dengan menjalankan perintah berikut:
aws ec2 describe-availability-zones --region us-east-1
Opsi satu: Membuat jaringan VPC di konsol Amazon MWAA
Bagian berikut menunjukkan cara membuat jaringan VPC Amazon di konsol Amazon MWAA. Opsi ini menggunakanRouting publik melalui Internet. Ini dapat digunakan untuk server Web Apache Airflow dengan jaringan pribadi atau mode akses jaringan publik.
Gambar berikut menunjukkan di mana Anda dapat menemukan tombol Create MWAA VPC di konsol Amazon MWAA.
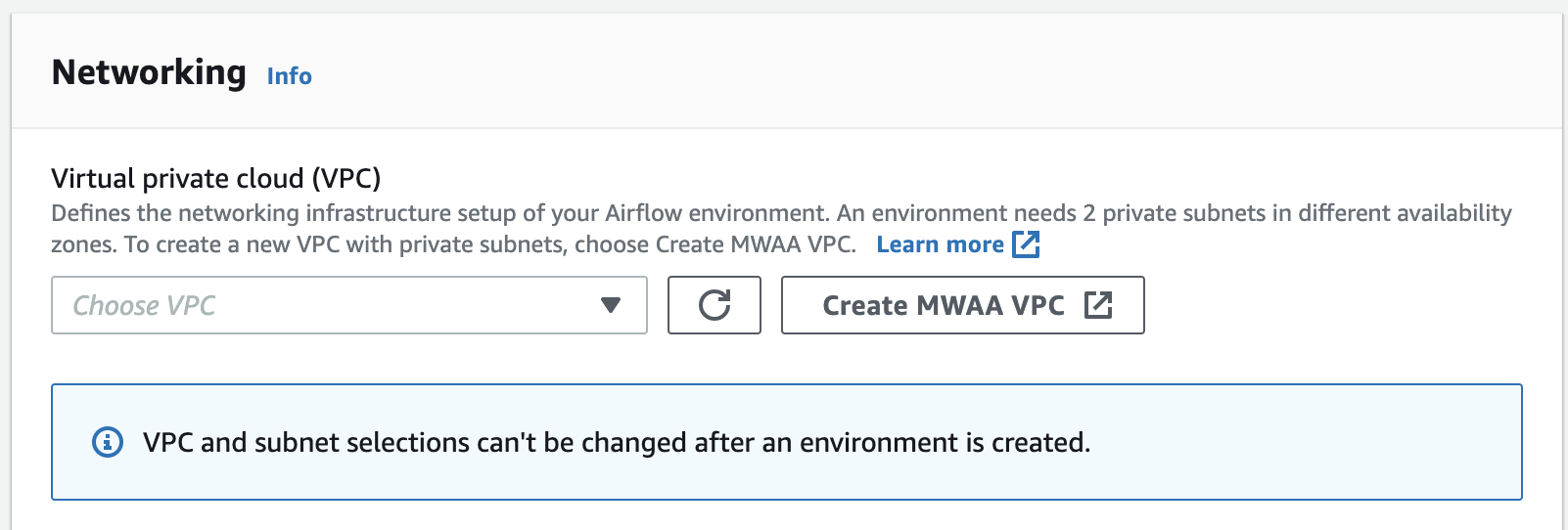
Opsi dua: Membuat jaringan VPC Amazon dengan akses Internet
AWS CloudFormation Template berikut membuat jaringan VPC Amazon dengan akses Internet di Wilayah default AWS Anda. Opsi ini menggunakanRouting publik melalui Internet. Template ini dapat digunakan untuk server Web Apache Airflow dengan jaringan Private atau mode akses jaringan Publik.
-
Salin isi template berikut dan simpan secara lokal sebagai
cfn-vpc-public-private.yaml. Anda juga dapat mengunduh template.Description: This template deploys a VPC, with a pair of public and private subnets spread across two Availability Zones. It deploys an internet gateway, with a default route on the public subnets. It deploys a pair of NAT gateways (one in each AZ), and default routes for them in the private subnets. Parameters: EnvironmentName: Description: An environment name that is prefixed to resource names Type: String Default: mwaa- VpcCIDR: Description: Please enter the IP range (CIDR notation) for this VPC Type: String Default: 10.192.0.0/16 PublicSubnet1CIDR: Description: Please enter the IP range (CIDR notation) for the public subnet in the first Availability Zone Type: String Default: 10.192.10.0/24 PublicSubnet2CIDR: Description: Please enter the IP range (CIDR notation) for the public subnet in the second Availability Zone Type: String Default: 10.192.11.0/24 PrivateSubnet1CIDR: Description: Please enter the IP range (CIDR notation) for the private subnet in the first Availability Zone Type: String Default: 10.192.20.0/24 PrivateSubnet2CIDR: Description: Please enter the IP range (CIDR notation) for the private subnet in the second Availability Zone Type: String Default: 10.192.21.0/24 Resources: VPC: Type: AWS::EC2::VPC Properties: CidrBlock: !Ref VpcCIDR EnableDnsSupport: true EnableDnsHostnames: true Tags: - Key: Name Value: !Ref EnvironmentName InternetGateway: Type: AWS::EC2::InternetGateway Properties: Tags: - Key: Name Value: !Ref EnvironmentName InternetGatewayAttachment: Type: AWS::EC2::VPCGatewayAttachment Properties: InternetGatewayId: !Ref InternetGateway VpcId: !Ref VPC PublicSubnet1: Type: AWS::EC2::Subnet Properties: VpcId: !Ref VPC AvailabilityZone: !Select [ 0, !GetAZs '' ] CidrBlock: !Ref PublicSubnet1CIDR MapPublicIpOnLaunch: true Tags: - Key: Name Value: !Sub ${EnvironmentName} Public Subnet (AZ1) PublicSubnet2: Type: AWS::EC2::Subnet Properties: VpcId: !Ref VPC AvailabilityZone: !Select [ 1, !GetAZs '' ] CidrBlock: !Ref PublicSubnet2CIDR MapPublicIpOnLaunch: true Tags: - Key: Name Value: !Sub ${EnvironmentName} Public Subnet (AZ2) PrivateSubnet1: Type: AWS::EC2::Subnet Properties: VpcId: !Ref VPC AvailabilityZone: !Select [ 0, !GetAZs '' ] CidrBlock: !Ref PrivateSubnet1CIDR MapPublicIpOnLaunch: false Tags: - Key: Name Value: !Sub ${EnvironmentName} Private Subnet (AZ1) PrivateSubnet2: Type: AWS::EC2::Subnet Properties: VpcId: !Ref VPC AvailabilityZone: !Select [ 1, !GetAZs '' ] CidrBlock: !Ref PrivateSubnet2CIDR MapPublicIpOnLaunch: false Tags: - Key: Name Value: !Sub ${EnvironmentName} Private Subnet (AZ2) NatGateway1EIP: Type: AWS::EC2::EIP DependsOn: InternetGatewayAttachment Properties: Domain: vpc NatGateway2EIP: Type: AWS::EC2::EIP DependsOn: InternetGatewayAttachment Properties: Domain: vpc NatGateway1: Type: AWS::EC2::NatGateway Properties: AllocationId: !GetAtt NatGateway1EIP.AllocationId SubnetId: !Ref PublicSubnet1 NatGateway2: Type: AWS::EC2::NatGateway Properties: AllocationId: !GetAtt NatGateway2EIP.AllocationId SubnetId: !Ref PublicSubnet2 PublicRouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref VPC Tags: - Key: Name Value: !Sub ${EnvironmentName} Public Routes DefaultPublicRoute: Type: AWS::EC2::Route DependsOn: InternetGatewayAttachment Properties: RouteTableId: !Ref PublicRouteTable DestinationCidrBlock: 0.0.0.0/0 GatewayId: !Ref InternetGateway PublicSubnet1RouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PublicRouteTable SubnetId: !Ref PublicSubnet1 PublicSubnet2RouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PublicRouteTable SubnetId: !Ref PublicSubnet2 PrivateRouteTable1: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref VPC Tags: - Key: Name Value: !Sub ${EnvironmentName} Private Routes (AZ1) DefaultPrivateRoute1: Type: AWS::EC2::Route Properties: RouteTableId: !Ref PrivateRouteTable1 DestinationCidrBlock: 0.0.0.0/0 NatGatewayId: !Ref NatGateway1 PrivateSubnet1RouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PrivateRouteTable1 SubnetId: !Ref PrivateSubnet1 PrivateRouteTable2: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref VPC Tags: - Key: Name Value: !Sub ${EnvironmentName} Private Routes (AZ2) DefaultPrivateRoute2: Type: AWS::EC2::Route Properties: RouteTableId: !Ref PrivateRouteTable2 DestinationCidrBlock: 0.0.0.0/0 NatGatewayId: !Ref NatGateway2 PrivateSubnet2RouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref PrivateRouteTable2 SubnetId: !Ref PrivateSubnet2 SecurityGroup: Type: AWS::EC2::SecurityGroup Properties: GroupName: "mwaa-security-group" GroupDescription: "Security group with a self-referencing inbound rule." VpcId: !Ref VPC SecurityGroupIngress: Type: AWS::EC2::SecurityGroupIngress Properties: GroupId: !Ref SecurityGroup IpProtocol: "-1" SourceSecurityGroupId: !Ref SecurityGroup Outputs: VPC: Description: A reference to the created VPC Value: !Ref VPC PublicSubnets: Description: A list of the public subnets Value: !Join [ ",", [ !Ref PublicSubnet1, !Ref PublicSubnet2 ]] PrivateSubnets: Description: A list of the private subnets Value: !Join [ ",", [ !Ref PrivateSubnet1, !Ref PrivateSubnet2 ]] PublicSubnet1: Description: A reference to the public subnet in the 1st Availability Zone Value: !Ref PublicSubnet1 PublicSubnet2: Description: A reference to the public subnet in the 2nd Availability Zone Value: !Ref PublicSubnet2 PrivateSubnet1: Description: A reference to the private subnet in the 1st Availability Zone Value: !Ref PrivateSubnet1 PrivateSubnet2: Description: A reference to the private subnet in the 2nd Availability Zone Value: !Ref PrivateSubnet2 SecurityGroupIngress: Description: Security group with self-referencing inbound rule Value: !Ref SecurityGroupIngress -
Di prompt perintah Anda, arahkan ke direktori tempat
cfn-vpc-public-private.yamldisimpan. Misalnya:cd mwaaproject -
Gunakan
aws cloudformation create-stackperintah untuk membuat tumpukan menggunakan AWS CLI.aws cloudformation create-stack --stack-name mwaa-environment --template-body file://cfn-vpc-public-private.yamlcatatan
Dibutuhkan sekitar 30 menit untuk membuat infrastruktur VPC Amazon.
Opsi tiga: Membuat jaringan VPC Amazon tanpa akses Internet
AWS CloudFormation Template berikut membuat jaringan VPC Amazon tanpa akses Internet di wilayah default AWS Anda.
Opsi ini menggunakanPerutean pribadi tanpa akses Internet. Template ini dapat digunakan untuk server Web Apache Airflow dengan mode akses jaringan Private saja. Ini menciptakan titik akhir VPC yang diperlukan untuk AWS layanan yang digunakan oleh lingkungan.
-
Salin isi template berikut dan simpan secara lokal sebagai
cfn-vpc-private.yaml. Anda juga dapat mengunduh template.AWSTemplateFormatVersion: "2010-09-09" Parameters: VpcCIDR: Description: The IP range (CIDR notation) for this VPC Type: String Default: 10.192.0.0/16 PrivateSubnet1CIDR: Description: The IP range (CIDR notation) for the private subnet in the first Availability Zone Type: String Default: 10.192.10.0/24 PrivateSubnet2CIDR: Description: The IP range (CIDR notation) for the private subnet in the second Availability Zone Type: String Default: 10.192.11.0/24 Resources: VPC: Type: AWS::EC2::VPC Properties: CidrBlock: !Ref VpcCIDR EnableDnsSupport: true EnableDnsHostnames: true Tags: - Key: Name Value: !Ref AWS::StackName RouteTable: Type: AWS::EC2::RouteTable Properties: VpcId: !Ref VPC Tags: - Key: Name Value: !Sub "${AWS::StackName}-route-table" PrivateSubnet1: Type: AWS::EC2::Subnet Properties: VpcId: !Ref VPC AvailabilityZone: !Select [ 0, !GetAZs '' ] CidrBlock: !Ref PrivateSubnet1CIDR MapPublicIpOnLaunch: false Tags: - Key: Name Value: !Sub "${AWS::StackName} Private Subnet (AZ1)" PrivateSubnet2: Type: AWS::EC2::Subnet Properties: VpcId: !Ref VPC AvailabilityZone: !Select [ 1, !GetAZs '' ] CidrBlock: !Ref PrivateSubnet2CIDR MapPublicIpOnLaunch: false Tags: - Key: Name Value: !Sub "${AWS::StackName} Private Subnet (AZ2)" PrivateSubnet1RouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref RouteTable SubnetId: !Ref PrivateSubnet1 PrivateSubnet2RouteTableAssociation: Type: AWS::EC2::SubnetRouteTableAssociation Properties: RouteTableId: !Ref RouteTable SubnetId: !Ref PrivateSubnet2 S3VpcEndoint: Type: AWS::EC2::VPCEndpoint Properties: ServiceName: !Sub "com.amazonaws.${AWS::Region}.s3" VpcEndpointType: Gateway VpcId: !Ref VPC RouteTableIds: - !Ref RouteTable SecurityGroup: Type: AWS::EC2::SecurityGroup Properties: VpcId: !Ref VPC GroupDescription: Security Group for Amazon MWAA Environments to access VPC endpoints GroupName: !Sub "${AWS::StackName}-mwaa-vpc-endpoints" SecurityGroupIngress: Type: AWS::EC2::SecurityGroupIngress Properties: GroupId: !Ref SecurityGroup IpProtocol: "-1" SourceSecurityGroupId: !Ref SecurityGroup SqsVpcEndoint: Type: AWS::EC2::VPCEndpoint Properties: ServiceName: !Sub "com.amazonaws.${AWS::Region}.sqs" VpcEndpointType: Interface VpcId: !Ref VPC PrivateDnsEnabled: true SubnetIds: - !Ref PrivateSubnet1 - !Ref PrivateSubnet2 SecurityGroupIds: - !Ref SecurityGroup CloudWatchLogsVpcEndoint: Type: AWS::EC2::VPCEndpoint Properties: ServiceName: !Sub "com.amazonaws.${AWS::Region}.logs" VpcEndpointType: Interface VpcId: !Ref VPC PrivateDnsEnabled: true SubnetIds: - !Ref PrivateSubnet1 - !Ref PrivateSubnet2 SecurityGroupIds: - !Ref SecurityGroup CloudWatchMonitoringVpcEndoint: Type: AWS::EC2::VPCEndpoint Properties: ServiceName: !Sub "com.amazonaws.${AWS::Region}.monitoring" VpcEndpointType: Interface VpcId: !Ref VPC PrivateDnsEnabled: true SubnetIds: - !Ref PrivateSubnet1 - !Ref PrivateSubnet2 SecurityGroupIds: - !Ref SecurityGroup KmsVpcEndoint: Type: AWS::EC2::VPCEndpoint Properties: ServiceName: !Sub "com.amazonaws.${AWS::Region}.kms" VpcEndpointType: Interface VpcId: !Ref VPC PrivateDnsEnabled: true SubnetIds: - !Ref PrivateSubnet1 - !Ref PrivateSubnet2 SecurityGroupIds: - !Ref SecurityGroup Outputs: VPC: Description: A reference to the created VPC Value: !Ref VPC MwaaSecurityGroupId: Description: Associates the Security Group to the environment to allow access to the VPC endpoints Value: !Ref SecurityGroup PrivateSubnets: Description: A list of the private subnets Value: !Join [ ",", [ !Ref PrivateSubnet1, !Ref PrivateSubnet2 ]] PrivateSubnet1: Description: A reference to the private subnet in the 1st Availability Zone Value: !Ref PrivateSubnet1 PrivateSubnet2: Description: A reference to the private subnet in the 2nd Availability Zone Value: !Ref PrivateSubnet2 -
Di prompt perintah Anda, arahkan ke direktori tempat
cfn-vpc-private.ymldisimpan. Misalnya:cd mwaaproject -
Gunakan
aws cloudformation create-stackperintah untuk membuat tumpukan menggunakan AWS CLI.aws cloudformation create-stack --stack-name mwaa-private-environment --template-body file://cfn-vpc-private.ymlcatatan
Dibutuhkan sekitar 30 menit untuk membuat infrastruktur VPC Amazon.
-
Anda harus membuat mekanisme untuk mengakses titik akhir VPC ini dari komputer Anda. Untuk mempelajari lebih lanjut, lihatMengelola akses ke titik akhir VPC Amazon khusus layanan di Amazon MWAA.
catatan
Anda selanjutnya dapat membatasi akses keluar di CIDR grup keamanan Amazon MWAA Anda. Misalnya, Anda dapat membatasi dirinya sendiri dengan menambahkan aturan keluar referensi sendiri, daftar awalan untuk Amazon S3, dan CIDR VPC Amazon Anda.
Apa selanjutnya?
-
Pelajari cara membuat lingkungan Amazon MWAA di. Buat lingkungan Amazon MWAA
-
Pelajari cara membuat terowongan VPN dari komputer Anda ke VPC Amazon Anda dengan perutean pribadi. Tutorial: Mengkonfigurasi akses jaringan pribadi menggunakan AWS Client VPN