Configure HTTPS encryption for Oracle JD Edwards EnterpriseOne on Oracle WebLogic by using an Application Load Balancer
Thanigaivel Thirumalai, Amazon Web Services
Summary
This pattern explains how to configure HTTPS encryption for SSL offloading in Oracle JD Edwards EnterpriseOne on Oracle WebLogic workloads. This approach encrypts traffic between the user’s browser and a load balancer to remove the encryption burden from the EnterpriseOne servers.
Many users scale the EnterpriseOne JAVA virtual machine (JVM) tier horizontally by using an AWS Application Load Balancer. The load balancer serves as the single point of contact for clients, and distributes incoming traffic across multiple JVMs. Optionally, the load balancer can distribute the traffic across multiple Availability Zones and increase the availability of EnterpriseOne.
The process described in this pattern configures encryption between the browser and the load balancer instead of encrypting the traffic between the load balancer and the EnterpriseOne JVMs. This approach is referred to as SSL offloading. Offloading the SSL decryption process from the EnterpriseOne web or application server to the Application Load Balancer reduces the burden on the application side. After SSL termination at the load balancer, the unencrypted traffic is routed to the application on AWS.
Oracle JD Edwards EnterpriseOne
Prerequisites and limitations
Prerequisites
An active AWS account
An AWS Identity and Access Management (IAM) role that has permissions to make AWS service calls and manage AWS resources
An SSL certificate
Product versions
This pattern was tested with Oracle WebLogic 12c, but you can also use other versions.
Architecture
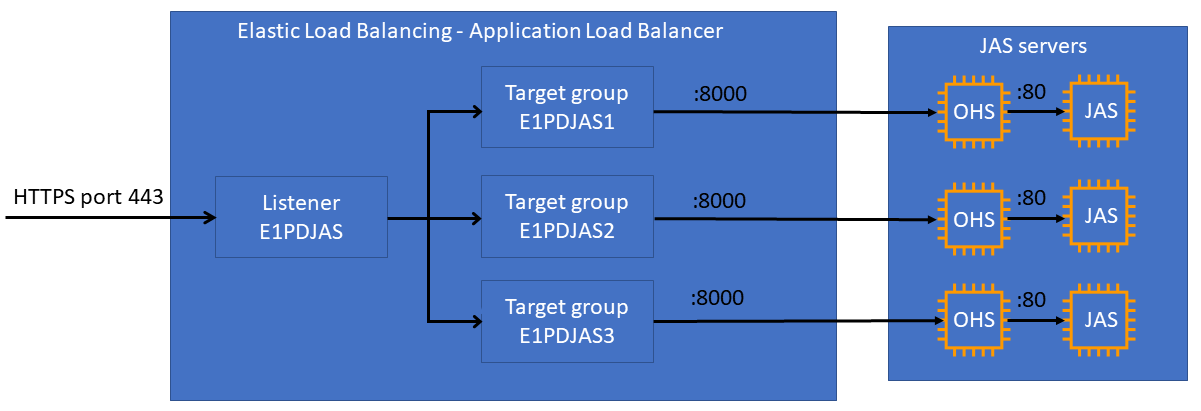
There are multiple approaches to perform SSL offloading. This pattern uses an Application Load Balancer and Oracle HTTP Server (OHS), as illustrated in the following diagram.

The following diagram shows the JD Edwards EnterpriseOne, Application Load Balancer, and Java Application Server (JAS) JVM layout.
Tools
AWS services
Application Load Balancers distribute incoming application traffic across multiple targets, such as Amazon Elastic Compute Cloud (Amazon EC2 instances), in multiple Availability Zones.
AWS Certificate Manager (ACM) helps you create, store, and renew public and private SSL/TLS X.509 certificates and keys that protect your AWS websites and applications.
Amazon Route 53 is a highly available and scalable DNS web service.
Best practices
For ACM best practices, see the ACM documentation.
Epics
| Task | Description | Skills required |
|---|---|---|
Install and configure Oracle components. |
| JDE CNC, WebLogic administrator |
Enable the WebLogic plugin at the domain level. | The WebLogic plugin is required for load balancing. To enable the plugin:
| JDE CNC, WebLogic administrator |
Edit the configuration file. | The
| JDE CNC, WebLogic administrator |
Start OHS by using the Enterprise Manager. |
| JDE CNC, WebLogic administrator |
| Task | Description | Skills required |
|---|---|---|
Set up a target group. |
For detailed instructions, see the Elastic Load Balancing documentation. | AWS administrator |
Set up the load balancer. |
| AWS administrator |
Add a Route 53 (DNS) record. | (Optional) You can add an Amazon Route 53 DNS record for the subdomain. This record would point to your Application Load Balancer. For instructions, see the Route 53 documentation. | AWS administrator |
Troubleshooting
| Issue | Solution |
|---|---|
HTTP server doesn’t appear. | If HTTP Server doesn’t appear in the Target Navigation list on the Enterprise Manager console, follow these steps:
When the instance has been created and changes have been activated, you will be able to see the HTTP server in the Target Navigation panel. |
Related resources
AWS documentation
Oracle documentation: