Connect to Application Migration Service data and control planes over a private network
Dipin Jain and Mike Kuznetsov, Amazon Web Services
Summary
This pattern explains how you can connect to an AWS Application Migration Service data plane and control plane on a private, secured network by using interface VPC endpoints.
Application Migration Service is a highly automated lift-and-shift (rehost) solution that simplifies, expedites, and reduces the cost of migrating applications to AWS. It enables companies to rehost a large number of physical, virtual, or cloud servers without compatibility issues, performance disruption, or long cutover windows. Application Migration Service is available from the AWS Management Console. This enables seamless integration with other AWS services, such as AWS CloudTrail, Amazon CloudWatch, and AWS Identity and Access Management (IAM).
You can connect from a source data center to a data plane—that is, to a subnet that serves as a staging area for data replication in the destination VPC—over a private connection by using AWS VPN services, AWS Direct Connect, or VPC peering in Application Migration Service. You can also use interface VPC endpoints powered by AWS PrivateLink to connect to an Application Migration Service control plane over a private network.
Prerequisites and limitations
Prerequisites
Staging area subnet – Before you set up Application Migration Service, create a subnet to be used as a staging area for data replicated from your source servers to AWS (that is, a data plane). You must specify this subnet in the Replication Settings template when you first access the Application Migration Service console. You can override this subnet for specific source servers in the Replication Settings template. Although you can use an existing subnet in your AWS account, we recommend that you create a new, dedicated subnet for this purpose.
Network requirements – The replication servers that are launched by Application Migration Service in your staging area subnet have to be able to send data to the Application Migration Service API endpoint at
https://mgn.<region>.amazonaws.com/, where<region>is the code for the AWS Region you are replicating to (for example,https://mgn.us-east-1.amazonaws.com). Amazon Simple Storage Service (Amazon S3) service URLs are required for downloading Application Migration Service software.The AWS Replication Agent installer should have access to the Amazon Simple Storage Service (Amazon S3) bucket URL of the AWS Region you are using with Application Migration Service.
The staging area subnet should have access to Amazon S3.
The source servers on which the AWS Replication Agent is installed must be able to send data to the replication servers in the staging area subnet and to the Application Migration Service API endpoint at
https://mgn.<region>.amazonaws.com/.
The following table lists the required ports.
Source | Destination | Port | For more information, see |
|---|---|---|---|
Source data center | Amazon S3 service URLs | 443 (TCP) | |
Source data center | AWS Region-specific console address for Application Migration Service | 443 (TCP) | Communication between the source servers and Application Migration Service over TCP port 443 |
Source data center | Staging area subnet | 1500 (TCP) | Communication between the source servers and the staging area subnet over TCP port 1500 |
Staging area subnet | AWS Region-specific console address for Application Migration Service | 443 (TCP) | Communication between the staging area subnet and Application Migration Service over TCP port 443 |
Staging area subnet | Amazon S3 service URLs | 443 (TCP) | |
Staging area subnet | Amazon Elastic Compute Cloud (Amazon EC2) endpoint of the subnet’s AWS Region | 443 (TCP) |
Limitations
Application Migration Service isn’t currently available in all AWS Regions and operating systems.
Architecture
The following diagram illustrates the network architecture for a typical migration. For more information about this architecture, see the Application Migration Service documentation and the Application Migration Service service architecture and network architecture video
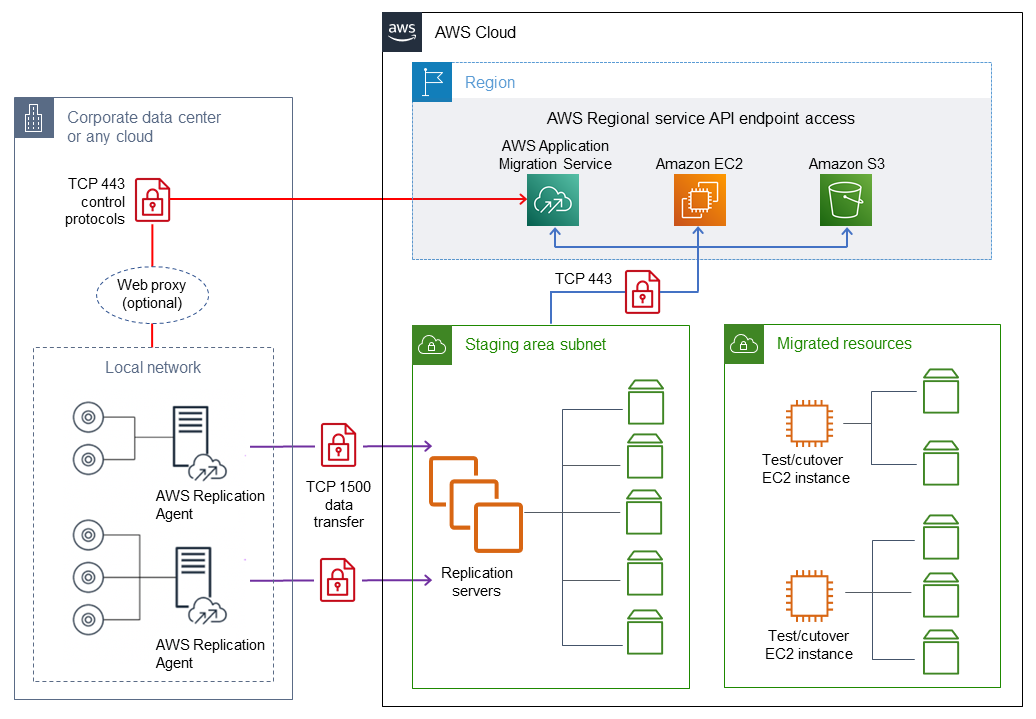
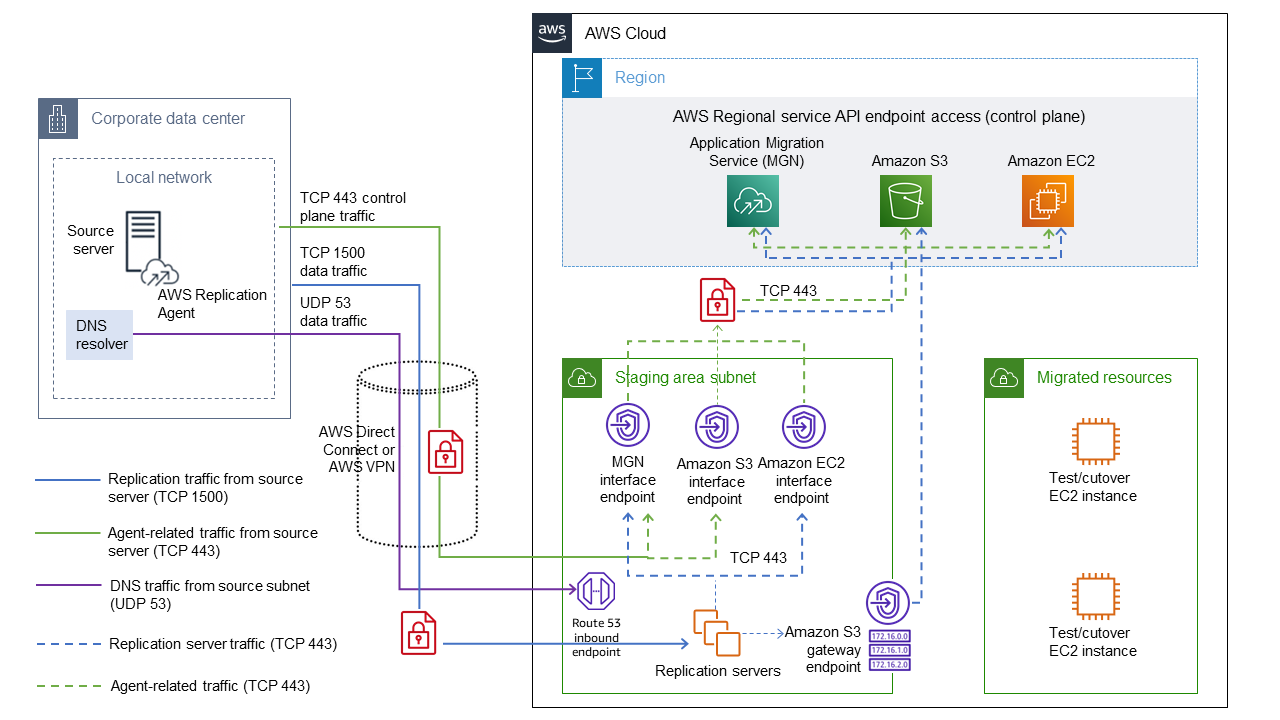
The following detailed view shows the configuration of interface VPC endpoints in the staging area VPC to connect Amazon S3 and Application Migration Service.
Tools
AWS Application Migration Service simplifies, expedites, and reduces the cost of rehosting applications on AWS.
Interface VPC endpoints enable you to connect to services that are powered by AWS PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Instances in your VPC do not require public IP addresses to communicate with resources in the service. Traffic between your VPC and the other service does not leave the Amazon network.
Epics
| Task | Description | Skills required |
|---|---|---|
Configure the interface endpoint for Application Migration Service. | The source data center and staging area VPC connect privately to the Application Migration Service control plane through the interface endpoint that you create in the target staging area VPC. To create the endpoint:
For more information, see Access an AWS service using an interface VPC endpoint in the Amazon VPC documentation. | Migration lead |
Configure the interface endpoint for Amazon EC2. | The staging area VPC connects privately to the Amazon EC2 API through the interface endpoint that you create in the target staging area VPC. To create the endpoint, follow the instructions provided in the previous story.
| Migration lead |
Configure the interface endpoint for Amazon S3. | The source data center and staging area VPC connect privately to the Amazon S3 API through the interface endpoint that you create in the target staging area VPC. To create the endpoint, follow the instructions provided in the first story.
NoteYou use an interface endpoint because gateway endpoint connections cannot be extended out of a VPC. (For details, see the AWS PrivateLink documentation.) | Migration lead |
Configure the Amazon S3 Gateway endpoint. | During the configuration phase, the replication server has to connect to an S3 bucket to download the AWS Replication Server’s software updates. However, Amazon S3 interface endpoints do not support private DNS names, and there is no way to supply an Amazon S3 endpoint DNS name to a replication server. To mitigate this issue, you create an Amazon S3 gateway endpoint in the VPC that the staging area subnet belongs to, and update the staging subnet’s route tables with the relevant routes. For more information, see Create a gateway endpoint in the AWS PrivateLink documentation. | Cloud administrator |
Configure on-premises DNS to resolve private DNS names for endpoints. | The interface endpoints for Application Migration Service and Amazon EC2 have private DNS names that can be resolved in the VPC. However, you also need to configure on-premises servers to resolve private DNS names for these interface endpoints. There are multiple ways to configure these servers. In this pattern, we tested this functionality by forwarding on-premises DNS queries to the Amazon Route 53 Resolver inbound endpoint in the staging area VPC. For more information, see Resolving DNS queries between VPCs and your network in the Route 53 documentation. | Migration engineer |
| Task | Description | Skills required |
|---|---|---|
Install AWS Replication Agent by using AWS PrivateLink. |
Here’s an example for Linux:
After you have established your connection with Application Migration Service and installed the AWS Replication Agent, follow the instructions in the Application Migration Service documentation to migrate your source servers to your target VPC and subnet. | Migration engineer |
Related resources
Application Migration Service documentation
Additional resources
Rehosting your applications in a multi-account architecture on AWS by using VPC interface endpoints (AWS Prescriptive Guidance guide)
AWS Application Migration Service – A Technical Introduction
(AWS Training and Certification walkthrough) AWS Application Migration Service architecture and network architecture
(video)
Additional information
Troubleshooting AWS Replication Agent installations on Linux servers
If you get a gcc error on an Amazon Linux server, configure the package repository and use the following command:
## sudo yum groupinstall "Development Tools"