Amazon Cognito user pools
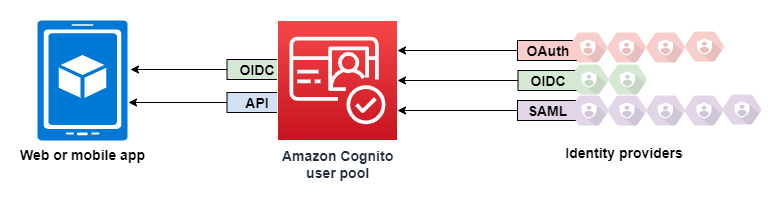
An Amazon Cognito user pool is a user directory for web and mobile app authentication and authorization. From the perspective of your app, an Amazon Cognito user pool is an OpenID Connect (OIDC) identity provider (IdP). A user pool adds layers of additional features for security, identity federation, app integration, and customization of the user experience.
You can, for example, verify that your users’ sessions are from trusted sources. You can combine the Amazon Cognito directory with an external identity provider. With your preferred AWS SDK, you can choose the API authorization model that works best for your app. And you can add AWS Lambda functions that modify or overhaul the default behavior of Amazon Cognito.
Topics
Features
Amazon Cognito user pools have the following features.
Sign-up
Amazon Cognito user pools have user-driven, administrator-driven, and programmatic methods to add user profiles to your user pool. Amazon Cognito user pools supports the following sign-up models. You can use any combination of these models in your app.
Important
If you activate user sign-up in your user pool, anyone on the internet can sign up for an account and sign into your apps. Don't enable self-registration in your user pool unless you want to open your app to public sign-up. To change this setting, update Self-service sign-up in the Sign-up menu under Authentication in the user pool console, or update the value of AllowAdminCreateUserOnly in a CreateUserPool or UpdateUserPool API request.
For information about security features that you can set up in your user pools, see Using Amazon Cognito user pools security features.
-
Your users can enter their information in your app and create a user profile that’s native to your user pool. You can call API sign-up operations to register users in your user pool. You can open these sign-up operations to anyone, or you can authorize them with a client secret or AWS credentials.
-
You can redirect users to a third-party IdP that they can authorize to pass their information to Amazon Cognito. Amazon Cognito processes OIDC id tokens, OAuth 2.0
userInfodata, and SAML 2.0 assertions into user profiles in your user pool. You control the attributes that you want Amazon Cognito to receive based on attribute-mapping rules. -
You can skip public or federated sign-up, and create users based on your own data source and schema. Add users directly in the Amazon Cognito console or API. Import users from a CSV file. Run a just-in-time AWS Lambda function that looks up your new user in an existing directory, and populates their user profile from existing data.
After your users sign up, you can add them to groups that Amazon Cognito lists in the access and ID tokens. You can also link user pool groups to IAM roles when you pass the ID token to an identity pool.
Related topics
Sign-in
Amazon Cognito can be a standalone user directory and identity provider (IdP) to your app. Your users can sign in with managed login pages that are hosted by Amazon Cognito, or with a custom-built user authentication service through the Amazon Cognito user pools API. The application tier behind your custom-built front end can authorize requests on the back end with any of several methods to confirm legitimate requests.
Users can set up and sign with usernames and passwords, passkeys, and email and SMS message one-time passwords. You can offer consolidate sign in with external user directories, multi-factor authentication (MFA) after sign-in, trust remembered devices, and custom authentication flows that you design.
To sign in users with an external directory, optionally combined with the user directory built in to Amazon Cognito, you can add the following integrations.
-
Sign in and import customer user data with OAuth 2.0 social sign-in. Amazon Cognito supports sign-in with Google, Facebook, Amazon, and Apple through OAuth 2.0.
-
Sign in and import work and school user data with SAML and OIDC sign-in. You can also configure Amazon Cognito to accept claims from any SAML or OpenID Connect (OIDC) identity provider (IdP).
-
Link external user profiles to native user profiles. A linked user can sign in with a third-party user identity and receive access that you assign to a user in the built-in directory.
Related topics
Machine-to-machine authorization
Some sessions aren’t a human-to-machine interaction. You might need a service account
that can authorize a request to an API by an automated process. To generate access tokens
for machine-to-machine authorization with OAuth 2.0 scopes, you can add an app client that
generates client-credentials grants
Related topics
Managed login
When you don’t want to build a user interface, you can present your users with a customized managed login pages. Managed login is a set of web pages for sign-up, sign-in, multi-factor authentication (MFA), and password reset. You can add managed login to your existing domain, or use a prefix identifier in an AWS subdomain.
Related topics
Security
Your local users can provide an additional authentication factor with a code from an SMS or email message, or an app that generates multi-factor authentication (MFA) codes. You can build mechanisms to set up and process MFA in your application, or you can let managed login manage it. Amazon Cognito user pools can bypass MFA when your users sign in from trusted devices.
If you don’t want to initially require MFA from your users, you can require it conditionally. With adaptive authentication, Amazon Cognito can detect potential malicious activity and require your user to set up MFA, or block sign-in.
If network traffic to your user pool might be malicious, you can monitor it and take action with AWS WAF web ACLs.
Related topics
Custom user experience
At most stages of a user’s sign-up, sign-in, or profile update, you can customize how Amazon Cognito handles the request. With Lambda triggers, you can modify an ID token or reject a sign-up request based on custom conditions. You can create your own custom authentication flow.
You can upload custom CSS and logos to give managed login a familiar look and feel to your users.
Related topics
Monitoring and analytics
Amazon Cognito user pools log API requests, including requests to managed login, to AWS CloudTrail. You can review performance metrics in Amazon CloudWatch Logs, push custom logs to CloudWatch with Lambda triggers, monitor email and SMS message delivery, and monitor API request volume in the Service Quotas console.
With the Plus feature plan, you can monitor user authentication attempts for indicators of compromise with automated-learning technology and immediately remediate risks. These advanced security features also log user activity to your user pool and optionally, to Amazon S3, CloudWatch Logs, or Amazon Data Firehose.
You can also log device and session data from your API requests to an Amazon Pinpoint campaign. With Amazon Pinpoint, you can send push notifications from your app based on your analysis of user activity.
Related topics
Amazon Cognito identity pools integration
The other half of Amazon Cognito is identity pools. Identity pools provide credentials that authorize and monitor API requests to AWS services, for example Amazon DynamoDB or Amazon S3, from your users. You can build identity-based access policies that protect your data based on how you classify the users in your user pool. Identity pools can also accept tokens and SAML 2.0 assertions from a variety of identity providers, independently of user pool authentication.