Terjemahan disediakan oleh mesin penerjemah. Jika konten terjemahan yang diberikan bertentangan dengan versi bahasa Inggris aslinya, utamakan versi bahasa Inggris.
Menerapkan aplikasi berbasis GRPC di cluster Amazon EKS dan mengaksesnya dengan Application Load Balancer
Kirankumar Chandrashekar dan Huy Nguyen, Amazon Web Services
Ringkasan
Pola ini menjelaskan cara meng-host aplikasi berbasis GRPC di cluster Amazon Elastic Kubernetes Service (Amazon EKS) dan mengaksesnya dengan aman melalui Application Load Balancer.
gRPC
Pola ini menunjukkan cara meng-host aplikasi berbasis GRPC yang berjalan pada pod Kubernetes di Amazon EKS. Klien gRPC terhubung ke Application Load Balancer melalui protokol HTTP/2 dengan koneksi terenkripsi. SSL/TLS Application Load Balancer meneruskan lalu lintas ke aplikasi gRPC yang berjalan pada pod Amazon EKS. Jumlah pod gRPC dapat secara otomatis diskalakan berdasarkan traffic dengan menggunakan Kubernetes Horizontal Pod Autoscaler. Kelompok target Application Load Balancer melakukan pemeriksaan kesehatan pada node Amazon EKS, mengevaluasi apakah targetnya sehat, dan meneruskan lalu lintas hanya ke node yang sehat.
Prasyarat dan batasan
Prasyarat
Akun AWS yang aktif.
Docker
, diinstal dan dikonfigurasi di Linux, macOS, atau Windows. AWS Command Line Interface (AWS CLI) versi 2, diinstal dan dikonfigurasi di Linux, macOS, atau Windows.
eksctl
, diinstal dan dikonfigurasi di Linux, macOS, atau Windows. kubectl, diinstal dan dikonfigurasi untuk mengakses sumber daya di kluster Amazon EKS Anda. Untuk informasi selengkapnya, lihat Menginstal atau memperbarui kubectl di dokumentasi Amazon EKS.g RPCurl
, diinstal dan dikonfigurasi. Cluster Amazon EKS baru atau yang sudah ada. Untuk informasi selengkapnya, lihat Memulai Amazon EKS.
Terminal komputer Anda dikonfigurasi untuk mengakses kluster Amazon EKS. Untuk informasi selengkapnya, lihat Mengonfigurasi komputer untuk berkomunikasi dengan klaster Anda di dokumentasi Amazon EKS.
AWS Load Balancer Controller, disediakan di klaster Amazon EKS.
Nama host DNS yang ada dengan SSL atau SSL/TLS sertifikat yang valid. Anda dapat memperoleh sertifikat untuk domain Anda dengan menggunakan AWS Certificate Manager (ACM) atau mengunggah sertifikat yang sudah ada ke ACM. Untuk informasi selengkapnya tentang kedua opsi ini, lihat Meminta sertifikat publik dan Mengimpor sertifikat ke AWS Certificate Manager dalam dokumentasi ACM.
Arsitektur
Diagram berikut menunjukkan arsitektur yang diterapkan oleh pola ini.
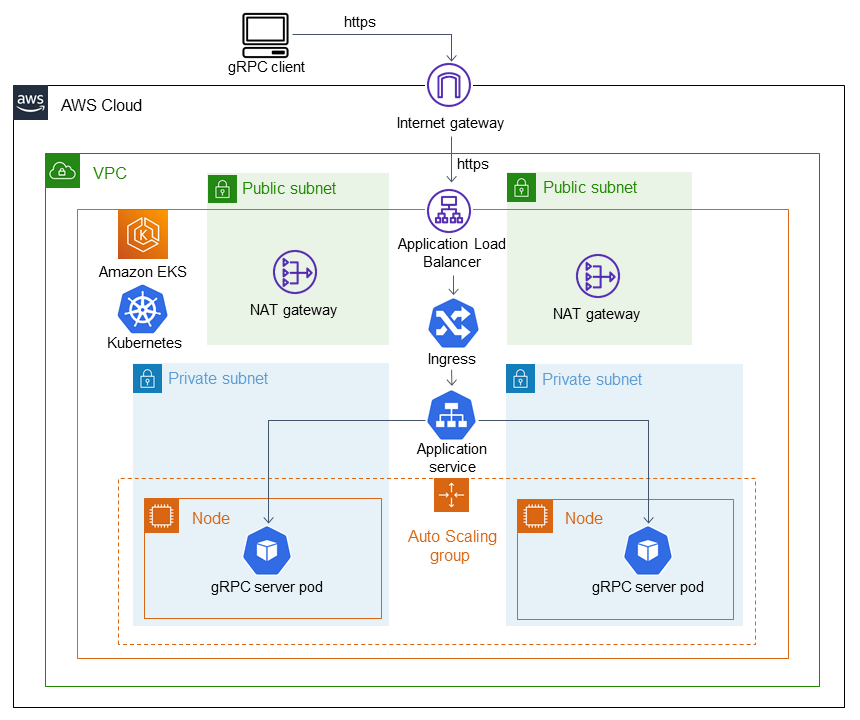
Diagram berikut menunjukkan alur kerja di mana SSL/TLS lalu lintas diterima dari klien gRPC yang diturunkan ke Application Load Balancer. Lalu lintas diteruskan dalam plaintext ke server gRPC karena berasal dari virtual private cloud (VPC).

Alat
Layanan AWS
AWS Command Line Interface (AWS CLI) adalah alat sumber terbuka yang membantu Anda berinteraksi dengan layanan AWS melalui perintah di shell baris perintah Anda.
Elastic Load Balancing mendistribusikan lalu lintas aplikasi atau jaringan yang masuk ke beberapa target. Misalnya, Anda dapat mendistribusikan lalu lintas di seluruh instans, container, dan alamat IP Amazon Elastic Compute Cloud (Amazon EC2) di satu atau beberapa Availability Zone.
Amazon Elastic Container Registry (Amazon ECR) adalah layanan registri gambar kontainer terkelola yang aman, terukur, dan andal.
Amazon Elastic Kubernetes Service (Amazon EKS) membantu Anda menjalankan Kubernetes di AWS tanpa perlu menginstal atau memelihara control plane atau node Kubernetes Anda sendiri.
Alat
eksctl
adalah alat CLI sederhana untuk membuat cluster di Amazon EKS. kubectl
adalah utilitas baris perintah untuk menjalankan perintah terhadap klaster Kubernetes. AWS Load Balancer Controller membantu Anda mengelola AWS Elastic Load Balancer untuk klaster Kubernetes.
g RPCurl
adalah alat baris perintah yang membantu Anda berinteraksi dengan layanan gRPC.
Repositori kode
Kode untuk pola ini tersedia di repositori GitHub grpc-traffic-on-alb-to-eks
Epik
| Tugas | Deskripsi | Keterampilan yang dibutuhkan |
|---|---|---|
Buat repositori Amazon ECR. | Masuk ke AWS Management Console, buka konsol Amazon ECR Anda juga dapat membuat repositori Amazon ECR dengan AWS CLI dengan menjalankan perintah berikut:
| Administrator awan |
membuat gambar Docker. |
| DevOps insinyur |
Dorong gambar Docker ke Amazon ECR. |
| DevOps insinyur |
| Tugas | Deskripsi | Keterampilan yang dibutuhkan |
|---|---|---|
Ubah nilai dalam file manifes Kubernetes. |
| DevOps insinyur |
Menerapkan file manifes Kubernetes. | Menerapkan
| DevOps insinyur |
| Tugas | Deskripsi | Keterampilan yang dibutuhkan |
|---|---|---|
Catat FQDN untuk Application Load Balancer. |
| DevOps insinyur |
| Tugas | Deskripsi | Keterampilan yang dibutuhkan |
|---|---|---|
Uji server gRPC. | Gunakan g RPCurl untuk menguji titik akhir dengan menjalankan perintah berikut:
catatanGanti | DevOps insinyur |
Uji server gRPC menggunakan klien gRPC. | Dalam Contoh kode berikut menunjukkan respon dari server gRPC untuk permintaan klien:
Ini menunjukkan bahwa klien dapat berbicara dengan server dan koneksi berhasil. | DevOps insinyur |
| Tugas | Deskripsi | Keterampilan yang dibutuhkan |
|---|---|---|
Hapus catatan DNS. | Hapus catatan DNS yang menunjuk ke FQDN Application Load Balancer yang Anda buat sebelumnya. | Administrator awan |
Lepaskan penyeimbang beban. | Di EC2 konsol Amazon | Administrator awan |
Hapus kluster Amazon EKS. | Hapus kluster Amazon EKS dengan menggunakan
| AWS DevOps |
Sumber daya terkait
Informasi tambahan
Sumber daya masuknya sampel:
--- apiVersion: networking.k8s.io/v1 kind: Ingress metadata: annotations: alb.ingress.kubernetes.io/healthcheck-protocol: HTTP alb.ingress.kubernetes.io/ssl-redirect: "443" alb.ingress.kubernetes.io/backend-protocol-version: "GRPC" alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS":443}]' alb.ingress.kubernetes.io/scheme: internet-facing alb.ingress.kubernetes.io/target-type: ip alb.ingress.kubernetes.io/certificate-arn: arn:aws:acm:<AWS-Region>:<AccountId>:certificate/<certificate_ID> labels: app: grpcserver environment: dev name: grpcserver namespace: grpcserver spec: ingressClassName: alb rules: - host: grpc.example.com # <----- replace this as per your host name for which the SSL certtficate is available in ACM http: paths: - backend: service: name: grpcserver port: number: 9000 path: / pathType: Prefix
Sumber daya penyebaran sampel:
apiVersion: apps/v1 kind: Deployment metadata: name: grpcserver namespace: grpcserver spec: selector: matchLabels: app: grpcserver replicas: 1 template: metadata: labels: app: grpcserver spec: containers: - name: grpc-demo image: <your_aws_account_id>.dkr.ecr.us-east-1.amazonaws.com/helloworld-grpc:1.0 #<------- Change to the URI that the Docker image is pushed to imagePullPolicy: Always ports: - name: grpc-api containerPort: 9000 env: - name: POD_IP valueFrom: fieldRef: fieldPath: status.podIP restartPolicy: Always
Keluaran sampel:
NAME CLASS HOSTS Address PORTS AGE grpcserver <none> <DNS-HostName> <ELB-address> 80 27d