Copy data from an S3 bucket to another account and Region by using the AWS CLI
Appasaheb Bagali and Purushotham G K, Amazon Web Services
Summary
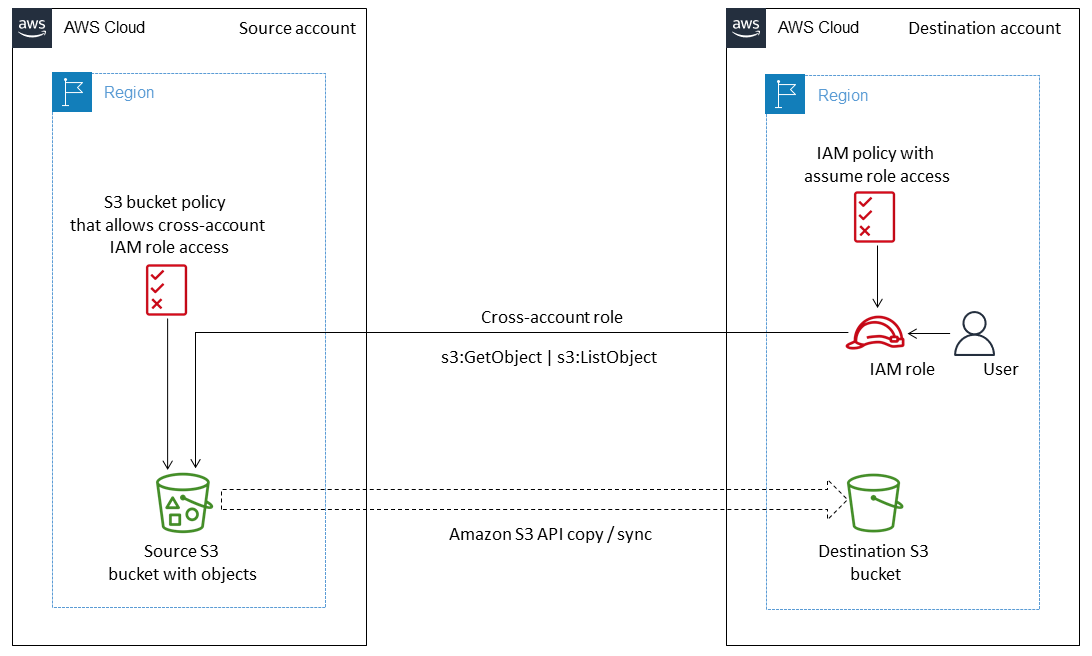
This pattern describes how to migrate data from an Amazon Simple Storage Service (Amazon S3) bucket in an AWS source account to a destination S3 bucket in another AWS account, either in the same AWS Region or in a different Region.
The source S3 bucket allows AWS Identity and Access Management (IAM) access by using an attached resource policy. A user in the destination account has to assume a role that has PutObject and GetObject permissions for the source bucket. Finally, you run copy and sync commands to transfer data from the source S3 bucket to the destination S3 bucket.
Accounts own the objects that they upload to S3 buckets. If you copy objects across accounts and Regions, you grant the destination account ownership of the copied objects. You can change the ownership of an object by changing its access control list (ACL) to bucket-owner-full-control. However, we recommend that you grant programmatic cross-account permissions to the destination account because ACLs can be difficult to manage for multiple objects.
Warning: This scenario requires IAM users with programmatic access and long-term credentials, which present a security risk. To help mitigate this risk, we recommend that you provide these users with only the permissions they require to perform the task and that you remove these users when they are no longer needed. Access keys can be updated if necessary. For more information, see Updating access keys in the IAM User Guide. |
|---|
This pattern covers one-time migration. For scenarios that require continuous and automatic migration of new objects from a source bucket to a destination bucket, you can use S3 Batch Replication instead, as described in the pattern Copy data from an S3 bucket to another account and Region by using S3 Batch Replication.
Prerequisites and limitations
Two active AWS accounts in the same or different AWS Regions.
An existing S3 bucket in the source account.
If your source or destination Amazon S3 bucket has default encryption enabled, you must modify the AWS Key Management Service (AWS KMS) key permissions. For more information, see the AWS re:Post article
on this topic. Familiarity with cross-account permissions.
Architecture
Tools
Amazon Simple Storage Service (Amazon S3) is a cloud-based object storage service that helps you store, protect, and retrieve any amount of data.
AWS Command Line Interface (AWS CLI) is an open-source tool that helps you interact with AWS services through commands in your command line shell.
AWS Identity and Access Management (IAM) helps you securely manage access to your AWS resources by controlling who is authenticated and authorized to use them.
Best practices
Security best practices in IAM (IAM documentation)
Applying least-privilege permissions (IAM documentation)
Epics
| Task | Description | Skills required |
|---|---|---|
Create an IAM user and get the access key. |
| AWS DevOps |
Create an IAM identity-based policy. | Create an IAM Identity-based policy named
NoteModify the source and destination bucket names according to your use case. This identity-based policy allows the user who is assuming this role to access the source bucket and destination bucket. | AWS DevOps |
Create an IAM role. | Create an IAM role named
NoteModify the Amazon Resource Name (ARN) of the destination IAM role or user name in the trust policy according to your use case. This trust policy allows the newly created IAM user to assume | AWS DevOps |
| Task | Description | Skills required |
|---|---|---|
Create and attach an S3 bucket policy. | Sign in to the AWS Management Console for your source account and open the Amazon S3 console. Choose your source S3 bucket and then choose Permissions. Under Bucket policy, choose Edit and then paste the following bucket policy. Choose Save.
NoteMake sure that you include the AWS account ID for the destination account and configure the bucket policy template according to your requirements. This resource-based policy allows the destination role | Cloud administrator |
| Task | Description | Skills required |
|---|---|---|
Create a destination S3 bucket. | Sign in to the AWS Management Console for your destination account, open the Amazon S3 console, and then choose Create bucket. Create an S3 bucket according to your requirements. For more information, see Creating a bucket in the Amazon S3 documentation. | Cloud administrator |
| Task | Description | Skills required |
|---|---|---|
Configure AWS CLI with the newly created user credentials. |
| AWS DevOps |
Assume the S3 migration role. |
For more information, see the AWS Knowledge Center | AWS administrator |
Copy and synchronize data from the source S3 bucket to the destination S3 bucket. | When you have assumed the role Copy (see the AWS CLI Command Reference
Synchronize (see the AWS CLI Command Reference
| Cloud administrator |
Troubleshooting
| Issue | Solution |
|---|---|
An error occurred ( |
|
Related resources
Creating an S3 bucket (Amazon S3 documentation)
Amazon S3 bucket policies and user policies (Amazon S3 documentation)
IAM identities (users, groups, and roles) (IAM documentation)
cp command
(AWS CLI documentation) sync command
(AWS CLI documentation)