Monitor IAM root user activity
JJ Sung and Mostefa Brougui, Amazon Web Services
Summary
Every Amazon Web Services (AWS) account has a root user. As a security best practice for AWS Identity and Access Management (IAM), we recommend that you use the root user to complete the tasks that only the root user can perform. For the complete list, see Tasks that require root user credentials in the AWS Account Management Reference Guide. Because the root user has full access to all of your AWS resources and billing information, we recommend that you don’t use this account and monitor it for any activity, which might indicate that the root user credentials have been compromised.
Using this pattern, you set up an event-driven architecture
When the IAM root user credentials are used, Amazon CloudWatch and AWS CloudTrail record the activity in the log and trail, respectively. In the spoke account, an Amazon EventBridge rule sends the event to the central event bus in the hub account. In the hub account, an EventBridge rule sends the event to an AWS Lambda function. The function uses an Amazon Simple Notification Service (Amazon SNS) topic that notifies you of the root user activity.
In this pattern, you use an AWS CloudFormation template to deploy the monitoring and event-handling services in the spoke accounts. You use a HashiCorp Terraform template to deploy the event-management and notification services in the hub account.
Prerequisites and limitations
Prerequisites
Permissions to deploy AWS resources in your AWS environment.
Permissions to deploy CloudFormation stack sets. For more information, see Prerequisites for stack set operations (CloudFormation documentation).
Terraform installed and ready to use. For more information, see Get Started – AWS
(Terraform documentation). An existing trail in each spoke account. For more information, see Getting started with AWS CloudTrail (CloudTrail documentation).
The trail is configured to send events to CloudWatch Logs. For more information, see Sending events to CloudWatch Logs (CloudTrail documentation).
Your hub and spoke accounts must be managed by AWS Organizations.
Architecture
The following diagram illustrates the building blocks of the implementation.
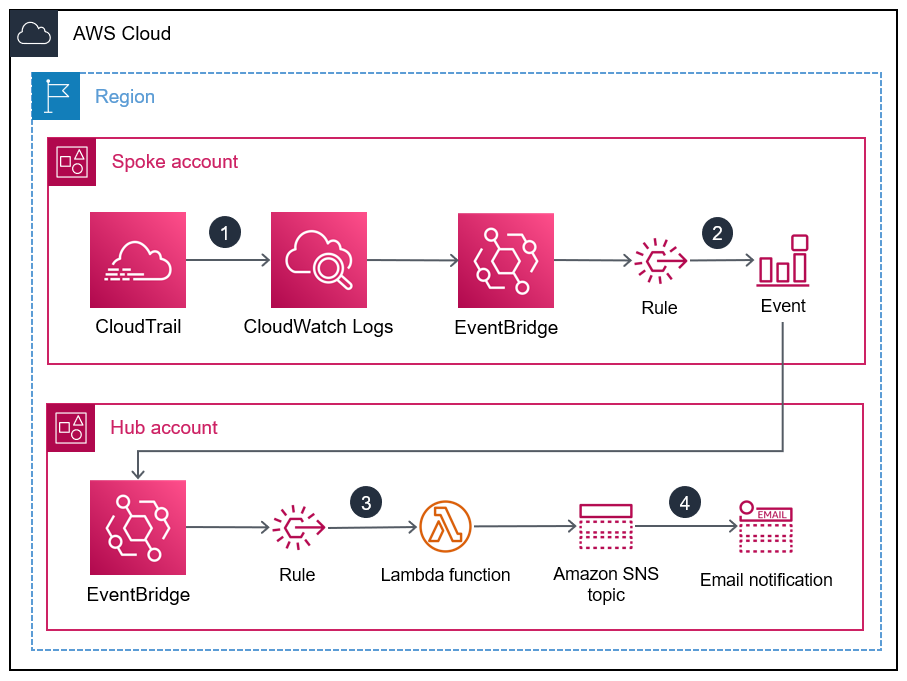
When the IAM root user credentials are used, CloudWatch and CloudTrail record the activity in the log and trail, respectively.
In the spoke account, an EventBridge rule sends the event to the central event bus in the hub account.
In the hub account, an EventBridge rule sends the event to a Lambda function.
The Lambda function uses an Amazon SNS topic that notifies you of the root user activity.
Tools
AWS services
AWS CloudFormation helps you set up AWS resources, provision them quickly and consistently, and manage them throughout their lifecycle across AWS accounts and Regions.
AWS CloudTrail helps you audit the governance, compliance, and operational risk of your AWS account.
Amazon CloudWatch Logs helps you centralize the logs from all your systems, applications, and AWS services so you can monitor them and archive them securely.
Amazon EventBridge is a serverless event bus service that helps you connect your applications with real-time data from a variety of sources. For example, AWS Lambda functions, HTTP invocation endpoints using API destinations, or event buses in other AWS accounts.
AWS Identity and Access Management (IAM) helps you securely manage access to your AWS resources by controlling who is authenticated and authorized to use them.
AWS Lambda is a compute service that helps you run code without needing to provision or manage servers. It runs your code only when needed and scales automatically, so you pay only for the compute time that you use.
Amazon Simple Notification Service (Amazon SNS) helps you coordinate and manage the exchange of messages between publishers and clients, including web servers and email addresses.
Other tools and services
Terraform
is a CLI application for provisioning and managing cloud infrastructure and resources by using code, in the form of configuration files.
Code repository
The source code and templates for this pattern are available in a GitHub repository
A Terraform template containing the resources you deploy in the hub account
A CloudFormation template you deploy as a stack set instance in the spoke accounts
The repository has the following overall structure.
. |__README.md |__spoke-stackset.yaml |__hub.tf |__root-activity-monitor-module |__main.tf # contains Terraform code to deploy resources in the Hub account |__iam # contains IAM policies JSON files |__ lambda-assume-policy.json # contains trust policy of the IAM role used by the Lambda function |__ lambda-policy.json # contains the IAM policy attached to the IAM role used by the Lambda function |__outputs # contains Lambda function zip code
The Epics section provides step-by-step instructions for deploying the templates.
Epics
| Task | Description | Skills required |
|---|---|---|
Clone the sample code repository. |
| General AWS |
Update the Terraform template. |
| General AWS |
Deploy the resources to the AWS hub account. |
| General AWS |
| Task | Description | Skills required |
|---|---|---|
Deploy the CloudFormation template. |
For more information and instructions, see Create a stack set (CloudFormation documentation). | General AWS |
| Task | Description | Skills required |
|---|---|---|
Use the root user credentials. |
| General AWS |
Related resources
Security best practices (IAM documentation)
Working with StackSets (CloudFormation documentation)
Get Started
(Terraform documentation)
Additional information
Amazon GuardDuty is a continuous security monitoring service that analyzes and processes logs to identify unexpected and potentially unauthorized activity in your AWS environment. As an alternative to this solution, if you have enabled GuardDuty, it can alert you when the root user credentials have been used. The GuardDuty finding is Policy:IAMUser/RootCredentialUsage, and the default severity is Low. For more information, see Managing Amazon GuardDuty findings.