Deploy preventative attribute-based access controls for public subnets
Joel Alfredo Nunez Gonzalez and Samuel Ortega Sancho, Amazon Web Services
Summary
In centralized network architectures, inspection and edge virtual private clouds (VPCs) concentrate all inbound and outbound traffic, such as traffic to and from the internet. However, this can create bottlenecks or result in reaching the limits of AWS service quotas. Deploying network edge security alongside the workloads in their VPCs provides unprecedented scalability in comparison to the more common, centralized approach. This is called a distributed edge architecture.
Although deploying public subnets in workload accounts can provide benefits, it also introduces new security risks because it increases the attack surface. We recommend that you deploy only Elastic Load Balancing (ELB) resources, such as Application Load Balancers, or NAT gateways in the public subnets of these VPCs. Using load balancers and NAT gateways in dedicated public subnets helps you implement fine-grained control for inbound and outbound traffic.
Attribute-based access control (ABAC) is the practice of creating fine-grained permissions based on user attributes, such as department, job role, and team name. For more information, see ABAC for AWS
This pattern describes how to help secure public subnets by implementing ABAC through a service control policy (SCP) in AWS Organizations and policies in AWS Identity and Access Management (IAM). You apply the SCP to either a member account of an organization or to an organizational unit (OU). These ABAC policies permit users to deploy NAT gateways in the target subnets and prevent them from deploying other Amazon Elastic Compute Cloud (Amazon EC2) resources, such as EC2 instances and elastic network interfaces.
Prerequisites and limitations
Prerequisites
An organization in AWS Organizations
Administrative access to the AWS Organizations root account
In the organization, an active member account or OU for testing the SCP
Limitations
The SCP in this solution doesn’t prevent AWS services that use a service-linked role from deploying resources in the target subnets. Examples of these services are Elastic Load Balancing (ELB), Amazon Elastic Container Service (Amazon ECS), and Amazon Relational Database Service (Amazon RDS). For more information, see SCP effects on permissions in the AWS Organizations documentation. Implement security controls to detect these exceptions.
Architecture
Target technology stack
SCP applied to an AWS account or OU in AWS Organizations
The following IAM roles:
AutomationAdminRole– Used to modify subnet tags and create VPC resources after implementing the SCPTestAdminRole– Used to test whether the SCP is preventing other IAM principals, including those with administrative access, from performing the actions reserved for theAutomationAdminRole
Target architecture
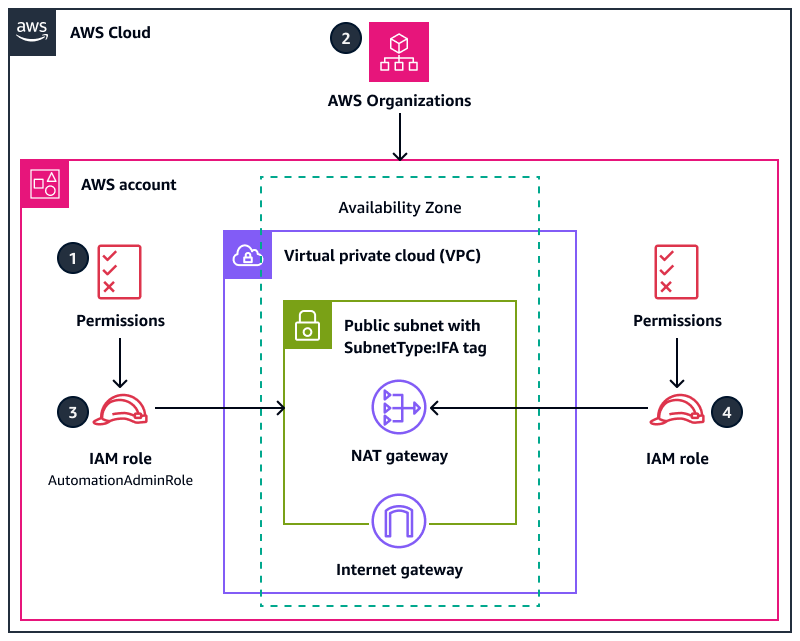
You create the
AutomationAdminRoleIAM role in the target account. This role has permissions to manage networking resources. Note the following permissions that are exclusive to this role:This role can create VPCs and public subnets.
This role can modify the tag assignments for the target subnets.
This role can manage its own permissions.
In AWS Organizations, you apply the SCP to the target AWS account or OU. For a sample policy, see Additional information in this pattern.
A user or a tool in the CI/CD pipeline can assume the
AutomationAdminRolerole to apply theSubnetTypetag to the target subnets.By assuming other IAM roles, authorized IAM principals in your organization can manage NAT gateways in the target subnets and other permitted networking resources in the AWS account, such as route tables. Use IAM policies to grant these permissions. For more information, see Identity and access management for Amazon VPC.
Automation and scale
To help protect public subnets, the corresponding AWS tags must be applied. After applying the SCP, NAT gateways are the only kind of Amazon EC2 resource that authorized users can create in subnets that have the SubnetType:IFA tag. (IFA means internet-facing assets.) The SCP prevents the creation of other Amazon EC2 resources, such as instances and elastic network interfaces. We recommend that you use a CI/CD pipeline that assumes the AutomationAdminRole role to create VPC resources so that these tags are properly applied to public subnets.
Tools
AWS services
AWS Identity and Access Management (IAM) helps you securely manage access to your AWS resources by controlling who is authenticated and authorized to use them.
AWS Organizations is an account management service that helps you consolidate multiple AWS accounts into an organization that you create and centrally manage. In AWS Organizations, you can implement service control policies (SCPs), which are a type of policy that you can use to manage permissions in your organization.
Amazon Virtual Private Cloud (Amazon VPC) helps you launch AWS resources into a virtual network that you’ve defined. This virtual network resembles a traditional network that you’d operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
Epics
| Task | Description | Skills required |
|---|---|---|
Create a test admin role. | Create an IAM role named | AWS administrator |
Create the automation admin role. |
The following is an example of a trust policy that you could use to test the role from the
| AWS administrator |
Create and attach the SCP. |
| AWS administrator |
| Task | Description | Skills required |
|---|---|---|
Create a VPC or subnet. |
| AWS administrator |
Manage tags. |
| AWS administrator |
Deploy resources in the target subnets. |
| AWS administrator |
Manage the AutomationAdminRole role. |
| AWS administrator |
| Task | Description | Skills required |
|---|---|---|
Clean up deployed resources. |
| AWS administrator |
Related resources
AWS documentation
Additional AWS references
Additional information
The following service control policy is an example that you can use to test this approach in your organization.
{ "Version": "2012-10-17", "Statement": [ { "Sid": "DenyVPCActions", "Effect": "Deny", "Action": [ "ec2:CreateVPC", "ec2:CreateRoute", "ec2:CreateSubnet", "ec2:CreateInternetGateway", "ec2:DeleteVPC", "ec2:DeleteRoute", "ec2:DeleteSubnet", "ec2:DeleteInternetGateway" ], "Resource": [ "arn:aws:ec2:*:*:*" ], "Condition": { "StringNotLike": { "aws:PrincipalARN": ["arn:aws:iam::*:role/AutomationAdminRole"] } } }, { "Sid": "AllowNATGWOnIFASubnet", "Effect": "Deny", "NotAction": [ "ec2:CreateNatGateway", "ec2:DeleteNatGateway" ], "Resource": [ "arn:aws:ec2:*:*:subnet/*" ], "Condition": { "ForAnyValue:StringEqualsIfExists": { "aws:ResourceTag/SubnetType": "IFA" }, "StringNotLike": { "aws:PrincipalARN": ["arn:aws:iam::*:role/AutomationAdminRole"] } } }, { "Sid": "DenyChangesToAdminRole", "Effect": "Deny", "NotAction": [ "iam:GetContextKeysForPrincipalPolicy", "iam:GetRole", "iam:GetRolePolicy", "iam:ListAttachedRolePolicies", "iam:ListInstanceProfilesForRole", "iam:ListRolePolicies", "iam:ListRoleTags" ], "Resource": [ "arn:aws:iam::*:role/AutomationAdminRole" ], "Condition": { "StringNotLike": { "aws:PrincipalARN": ["arn:aws:iam::*:role/AutomationAdminRole"] } } } ] }