Migrate an Amazon RDS for Oracle database to another AWS account and AWS Region using AWS DMS for ongoing replication
Durga Prasad Cheepuri and Eduardo Valentim, Amazon Web Services
Summary
Warning: IAM users have long-term credentials, which presents a security risk. To help mitigate this risk, we recommend that you provide these users with only the permissions they require to perform the task and that you remove these users when they are no longer needed. |
|---|
This pattern walks you through the steps for migrating an Amazon Relational Database Service (Amazon RDS) for Oracle source database to a different AWS account and AWS Region. The pattern uses a DB snapshot for a one-time full data load, and enables AWS Database Migration Service (AWS DMS) for ongoing replication.
Prerequisites and limitations
Prerequisites
An active AWS account that contains the source Amazon RDS for Oracle database, which has been encrypted using a non-default AWS Key Management Service (AWS KMS) key
An active AWS account in a different AWS Region from the source database, to use for the target Amazon RDS for Oracle database
Virtual private cloud (VPC) peering between the source and target VPCs
Familiarity with using an Oracle database as a source for AWS DMS
Familiarity with using an Oracle database as a target for AWS DMS
Product versions
Oracle versions 11g (versions 11.2.0.3.v1 and later) and up to 12.2, and 18c. For the latest list of supported versions and editions, see Using an Oracle Database as a Source for AWS DMS and with Using an Oracle database as a target for AWS DMS in the AWS documentation. For Oracle versions supported by Amazon RDS, see Oracle on Amazon RDS.
Architecture
Source and target technology stacks
Amazon RDS for Oracle DB instance
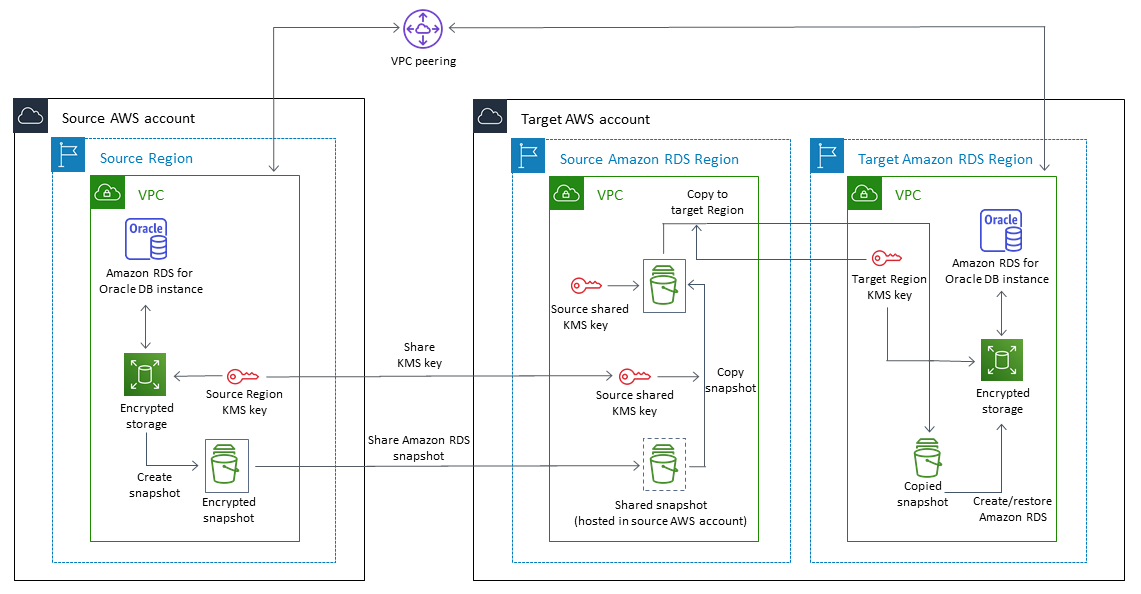
Ongoing replication architecture

Tools
Tools used for one-time full data load
Amazon Relational Database Service (Amazon RDS) creates a storage volume snapshot of your DB instance, backing up the entire DB instance and not just individual databases. When you create a DB snapshot, you need to identify which DB instance you are going to back up, and then give your DB snapshot a name so you can restore from it later. The amount of time it takes to create a snapshot varies with the size of your databases. Because the snapshot includes the entire storage volume, the size of files, such as temporary files, also affects the amount of time it takes to create the snapshot. For more information about using DB snapshots, see Creating a DB Snapshot in the Amazon RDS documentation.
AWS Key Management Service (AWS KMS) creates a key for Amazon RDS encryption. When you create an encrypted DB instance, you can also supply the AWS KMS key identifier for your encryption key. If you don't specify an AWS KMS key identifier, Amazon RDS uses your default encryption key for your new DB instance. AWS KMS creates your default encryption key for your AWS account. Your AWS account has a different default encryption key for each AWS Region. For this pattern, the Amazon RDS DB instance should be encrypted using the non-default AWS KMS key. For more information about using AWS KMS keys for Amazon RDS encryption, see Encrypting Amazon RDS resources in the Amazon RDS documentation.
Tools used for ongoing replication
AWS Database Migration Service (AWS DMS) is used to replicate ongoing changes and to keep the source and target databases in sync. For more information about using AWS DMS for ongoing replication, see Working with an AWS DMS replication instance in the AWS DMS documentation.
Epics
| Task | Description | Skills required |
|---|---|---|
Prepare the source Oracle DB instance. | Let the Amazon RDS for Oracle DB instance run in ARCHIVELOG mode, and set the retention period. For details, see Working with an AWS managed Oracle database as a source for AWS DMS. | DBA |
Set supplemental logging for the source Oracle DB instance. | Set database-level and table-level supplemental logging for the Amazon RDS for Oracle DB instance. For details, see Working with an AWS managed Oracle database as a source for AWS DMS. | DBA |
Update the AWS KMS key policy in the source account. | Update the AWS KMS key policy in the source AWS account to allow the target AWS account to use the encrypted Amazon RDS AWS KMS key. For details, see the AWS KMS documentation. | SysAdmin |
Create a manual Amazon RDS DB snapshot of the source DB instance. | AWS IAM user | |
Share the manual, encrypted Amazon RDS snapshot with the target AWS account. | For details, see Sharing a DB snapshot. | AWS IAM user |
| Task | Description | Skills required |
|---|---|---|
Attach a policy. | In the target AWS account, attach an AWS Identity and Access Management (IAM) policy to the root IAM user, to allow the IAM user to copy an encrypted DB snapshot using the shared AWS KMS key. | SysAdmin |
Switch to the source AWS Region. | AWS IAM user | |
Copy the shared snapshot. | In the Amazon RDS console, in the Snapshots pane, choose Shared with Me, and select the shared snapshot. Copy the snapshot to the same AWS Region as the source database by using the Amazon Resource Name (ARN) for the AWS KMS key used by the source database. For details, see Copying a DB snapshot. | AWS IAM user |
Switch to the target AWS Region, and create a new AWS KMS key. | AWS IAM user | |
Copy the snapshot. | Switch to the source AWS Region. On the Amazon RDS console, in the Snapshots pane, choose Owned by Me, and select the copied snapshot. Copy the snapshot to the target AWS Region by using the AWS KMS key for the new target AWS Region. | AWS IAM user |
Restore the snapshot. | Switch to the target AWS Region. On the Amazon RDS console, in the Snapshots pane, choose Owned by Me. Select the copied snapshot and restore it to an Amazon RDS for Oracle DB instance. For details, see Restoring from a DB snapshot. | AWS IAM user |
| Task | Description | Skills required |
|---|---|---|
Create an Oracle user with the appropriate permissions. | Create an Oracle user with the required privileges for Oracle as a source for AWS DMS. For details, see the AWS DMS documentation. | DBA |
Configure the source database for Oracle LogMiner or Oracle Binary Reader. | DBA |
| Task | Description | Skills required |
|---|---|---|
Create an Oracle user with the appropriate permissions. | Create an Oracle user with the required privileges for Oracle as a target for AWS DMS. For details, see the AWS DMS documentation. | DBA |
| Task | Description | Skills required |
|---|---|---|
Create a replication instance in the target AWS Region. | Create a replication instance in the VPC of the target AWS Region. For details, see the AWS DMS documentation. | AWS IAM user |
Create source and target endpoints with required encryption, and test connections. | For details, see the AWS DMS documentation. | DBA |
Create replication tasks. |
For details, see the AWS DMS documentation. | IAM user |
Start the tasks and monitor them. | For details, see the AWS DMS documentation. | AWS IAM user |
Enable validation on the task if needed. | Note that enabling validation does have a performance impact on the replication. For details, see the AWS DMS documentation. | AWS IAM user |
Related resources
How do I share manual Amazon RDS DB snapshots or DB cluster snapshots with another AWS account?
(AWS Knowledge Center article)