Choosing AWS security, identity, and governance services
Taking the first step
|
Time to read
|
27 minutes
|
|
Purpose
|
Help you determine which AWS security, identity, and governance
services are the best fit for your organization.
|
|
Last updated
|
December 30, 2024
|
|
Services covered
|
|
|
Introduction
Security, identity, and governance in the cloud are important components for you in
achieving and maintaining integrity and safety for your data and services. This is
especially relevant as more businesses migrate to cloud providers such as Amazon Web Services
(AWS).
This guide helps you select the AWS security, identity, and
governance services and tools that are the best fit for your needs
and your organization.
First, let's explore what we mean by security, identity, and
governance:
-
Cloud security refers to using
measures and practices to protect digital assets from threats. This includes
both the physical security of data centers and cybersecurity measures to guard
against online threats. AWS prioritizes security through encrypted data
storage, network security, and continuous monitoring of potential threats.
-
Identity
services help you securely manage identities,
resources, and permissions in a scalable way. AWS provides
identity services designed for workforce and customer-facing
applications, and for managing access to your workloads and
applications.
-
Cloud
governance is a set of rules, processes, and reports that guide your
organization to follow best practices. You can establish cloud governance across
your AWS resources, use built-in best practices and standards, and automate
compliance and auditing processes. Compliance in the cloud refers to adhering to laws and regulations
governing data protection and privacy. AWS Compliance Programs provides
information about the certifications, regulations, and frameworks that AWS
aligns with.
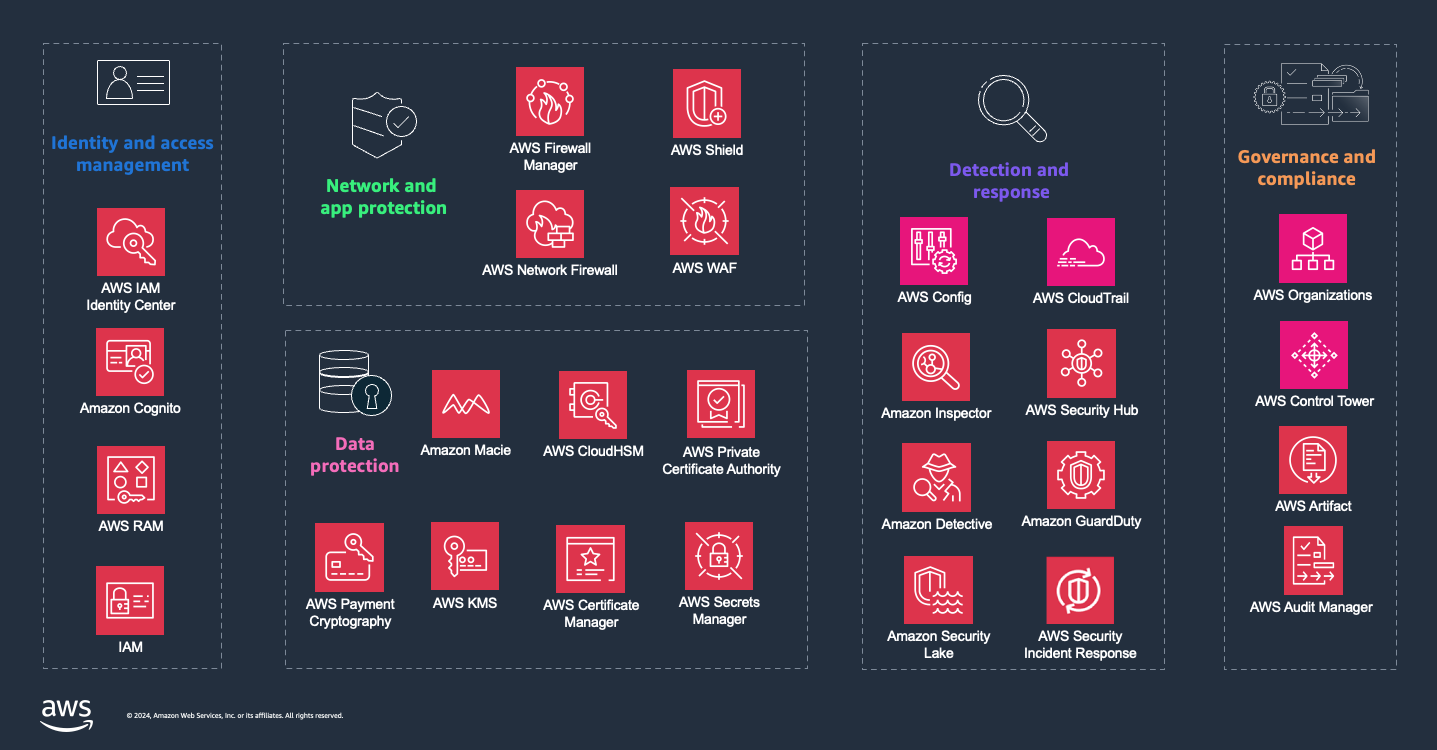
Understand AWS security, identity, and governance services
Security and compliance are shared responsibilities
Before choosing your AWS security, identity, and governance services, it's important for
you to understand that security and compliance are shared responsibilities between you
and AWS.
The nature of this shared responsibility helps relieve your operational burden, and it
provides you with flexibility and control over your deployment. This differentiation of
responsibility is commonly referred to as security "of" the
cloud and security "in" the cloud.
With an understanding of this model, you can understand the range of options available to
you, and how the applicable AWS services fit together.
As shown in the previous diagram, AWS offers tools and services across five domains to
help you achieve and maintain robust security, identity management, and governance in the
cloud. You can use AWS services across these five domains to help you do the following:
-
Form a multilayered approach to safeguarding your data and environments
-
Fortify your cloud infrastructure against evolving threats
-
Adhere to strict regulatory standards
To learn more about AWS security, including security documentation for AWS services,
see AWS Security Documentation.
In the following sections, we examine each domain further.
Understand AWS identity and access
management services
At the center of AWS security is the principle of least privilege: individuals and
services have only the access that they need. AWS IAM Identity Center is the recommended
AWS service for managing user access to AWS resources. You can use this service to
manage access to your accounts and permissions within those accounts, including identities
from external identity providers.
The following table summarizes the identity and access management offerings discussed
in this guide:
- AWS IAM Identity Center
AWS IAM Identity Center
helps you connect your source of identities, or create users.
You can centrally manage workforce access to multiple AWS accounts and applications.
- Amazon Cognito
Amazon Cognito
provides an identity tool for web and mobile apps to authenticate and authorize
users from the built-in user directory, your enterprise directory, and consumer
identity providers.
- AWS RAM
-
AWS RAM
helps you securely share your resources across AWS accounts, within your
organization, and with IAM roles and users.
- IAM
-
IAM
enables secure, fine-grained control over access to AWS workload resources.
Understand AWS data protection services
Data protection is vital in the cloud, and AWS provides services that help you
protect your data, accounts, and workloads. For example, encrypting your data both in transit and at rest helps protect it from exposure.
With AWS Key Management Service (AWS KMS) and AWS CloudHSM you can create and control
the cryptographic keys that you use to protect your data.
The following table summarizes the data protection offerings discussed in this guide:
- Amazon Macie
Amazon Macie
discovers sensitive data by using machine learning and pattern matching, and
enables automated protection against associated risks.
- AWS KMS
AWS KMS
creates and controls the cryptographic keys that you use to protect your data.
- AWS CloudHSM
AWS CloudHSM
provides highly available, cloud-based hardware security modules (HSMs).
- AWS Certificate Manager
AWS Certificate Manager
handles the complexity of creating, storing, and renewing public and private
SSL/TLS X.509 certificates and keys.
- AWS Private CA
AWS Private CA
helps you create private certificate authority hierarchies, including root and
subordinate certificate authorities (CAs).
- AWS Secrets Manager
AWS Secrets Manager
helps you manage, retrieve, and rotate database credentials, application
credentials, OAuth tokens, API keys, and other secrets.
- AWS Payment Cryptography
-
AWS Payment Cryptography
provides access to cryptographic functions and key management used in payment processing in accordance
with payment card industry (PCI) standards.
Understand AWS network and application
protection services
AWS offers several services to protect your networks and applications. AWS Shield
provides you with protection against Distributed Denial of Service (DDoS) attacks, and
AWS WAF helps you protect web applications from common web exploitation
attacks.
The following table summarizes the network and application protection offerings
discussed in this guide:
- AWS Firewall Manager
-
AWS Firewall Manager
simplifies your administration and maintenance tasks across multiple accounts
and resources for protection.
- AWS Network Firewall
-
AWS Network Firewall
provides a stateful, managed network firewall and intrusion detection and
prevention service with your VPC.
- AWS Shield
AWS Shield
provides protections against DDoS attacks for AWS resources at the network,
transport, and application layers.
- AWS WAF
AWS WAF
provides a web application firewall so you can monitor the HTTP(S) requests that
are forwarded to your protected web application resources.
Understand AWS detection and response services
AWS provides tools to help you streamline security operations across your AWS
environment, including multi-account
environments. For example, you can use Amazon GuardDuty for intelligent threat
detection, and you can use Amazon Detective to
identify and analyze security findings by collecting log data. AWS Security Hub supports
multiple security standards and provides an overview of security alerts and compliance
status across AWS accounts. AWS CloudTrail tracks
user activity and application programming interface (API) usage, which is crucial for
understanding and responding to security events.
The following table summarizes the detection and response offerings discussed in this
guide:
- AWS Config
AWS Config
provides a detailed view of the configuration of AWS resources in your
AWS account.
- AWS CloudTrail
-
AWS CloudTrail
records actions taken by a user, role, or AWS service.
- AWS Security Hub
AWS Security Hub
provides a comprehensive view of your security state in AWS.
- Amazon GuardDuty
Amazon GuardDuty
continuously monitors your AWS accounts, workloads, runtime activity, and data for malicious activity.
- Amazon Inspector
Amazon Inspector
scans your AWS workloads for software vulnerabilities and unintended network
exposure.
- Amazon Security Lake
-
Amazon Security Lake
automatically centralizes security data from AWS environments, SaaS providers,
on-premises environments, cloud sources, and third-party sources into a data lake.
- Amazon Detective
Amazon Detective
helps you analyze, investigate, and quickly identify the root cause of security
findings or suspicious activities.
- AWS Security Incident Response
AWS Security Incident Response
Helps you quickly prepare for, respond to, and receive guidance to help recover from security incidents.
Understand AWS governance and compliance services
AWS provides tools that help you adhere to your security, operational, compliance,
and cost standards. For example, you can use AWS Control Tower to set
up and govern a multi-account environment with prescriptive controls. With AWS Organizations, you can set up policy-based management for multiple accounts within
your organization.
AWS also gives you a comprehensive view of your compliance status and continuously
monitors your environment by using automated compliance checks based on the AWS best
practices and industry standards that your organization follows. For example, AWS Artifact
provides on-demand access to compliance reports, and AWS Audit Manager automates evidence
collection so that you can more easily assess whether your controls are operating
effectively.
The following table summarizes the governance and compliance offerings discussed in
this guide:
- AWS Organizations
-
AWS Organizations
helps you consolidate multiple AWS accounts into an organization that you
create and centrally manage.
- AWS Control Tower
AWS Control Tower
helps you set up and govern an AWS multi-account environment that's based on
best practices.
- AWS Artifact
AWS Artifact
provides on-demand downloads of AWS security and compliance documents.
- AWS Audit Manager
AWS Audit Manager
Helps you continuously audit your AWS usage to simplify how you assess risk
and compliance.
Consider AWS security, identity, and governance criteria
Choosing the right security, identity, and governance services on AWS depends on your
specific requirements and use cases.
Deciding to adopt an AWS security service
provides a decision tree to help you decide if adopting AWS services for
security, identity, and governance is suitable for your organization.
In addition, here are some criteria to
consider when making your decision about which services to use.
- Security requirements and threat landscape
-
Conduct a comprehensive assessment of your organization's specific
vulnerabilities and threats. This involves identifying the types of data that
you handle, such as personal customer information, financial records, or proprietary
business data. Understand the potential risks associated with each.
Assess your application and infrastructure architecture.
Determine whether your applications are public-facing and what kind of web traffic they
handle. This factors into your need for services such as AWS WAF to protect against web
exploitation. For internal applications, consider the importance of internal threat
detection and continuous monitoring with Amazon GuardDuty, which can identify unusual access
patterns or unauthorized deployments.
Finally, consider the sophistication of your existing security
posture and the expertise of your security team. If your team has limited
resources, choosing services that offer more automation and integration can provide you
with effective security enhancements, without overwhelming your team. Example services
include AWS Shield for DDoS protection and AWS Security Hub for centralized security monitoring.
- Compliance and regulatory requirements
-
Identify the relevant laws and standards for your
industry or geographic region, such as General Data Protection Regulation (GDPR), the
U.S. Health Insurance
Portability and Accountability Act of 1996 (HIPAA), or Payment Card Industry Data Security
Standard (PCI DSS).
AWS offers services such as AWS Config and AWS Artifact to help you manage
compliance with various standards. With AWS Config, you can assess, audit, and evaluate the
configurations of your AWS resources, making it easier for you to ensure compliance with
internal policies and regulatory requirements. AWS Artifact provides on-demand access to
AWS compliance documentation, aiding you with audits and compliance reporting.
Choosing services that align with your specific compliance needs can help your
organization meet legal requirements and build a secure and trustworthy environment for
your data. Explore AWS Compliance
Programs to learn more.
- Scalability and flexibility
-
Consider how your organization will grow, and how fast. Choose AWS services that will
help your security measures grow seamlessly with your infrastructure and adapt to evolving
threats.
To help you scale quickly, AWS Control Tower orchestrates the
capabilities of several other AWS services,
including AWS Organizations and AWS IAM Identity Center, to build a landing zone in less than an hour. Control
Tower sets up and manages resources on your behalf.
AWS also designs many services to automatically scale
with an application's traffic and usage patterns, such as Amazon GuardDuty for threat detection
and AWS WAF for protecting web applications. As your business scales up, these services
scale with it, without requiring manual adjustments or causing bottlenecks.
In addition, it's critical that you can customize your security
controls to match your business requirements and threat landscapes. Consider
managing your accounts with AWS Organizations, so you can manage 40+
services' resources across multiple accounts. This gives individual application
teams the flexibility and visibility to manage security needs that are specific to their
workload, while also giving them governance and visibility to centralized security teams.
Considering scalability and flexibility helps you ensure that your security posture is
robust, responsive, and capable of supporting dynamic business environments.
- Integration with existing systems
-
Consider security measures that enhance, rather than disrupt, your current operations. For
example, consider the following:
-
Streamline your workflows by aggregating security
data and alerts from AWS services and analyzing them alongside existing security
information and event management (SIEM) systems.
-
Create a unified view of security threats and
vulnerabilities across both AWS and on-premises environments.
-
Integrate AWS CloudTrail with existing log management solutions for comprehensive monitoring of user activities and API usage across your
AWS infrastructure and existing applications.
-
Examine ways that you can optimize resource
utilization and consistently apply security policies across environments.
This helps you reduce the risk of gaps in security coverage.
- Cost and budget considerations
-
Review the pricing models for each service
that you're considering. AWS often charges based on usage, such as the number of API
calls, the volume of data processed, or the amount of data stored. For example, Amazon GuardDuty
charges based on the amount of log data analyzed for threat detection, while AWS WAF
bills are based on the number of rules deployed and the number of web requests received.
Estimate your expected usage to forecast costs
accurately. Consider both current needs and potential growth or spikes in demand. For
example, scalability is a key feature of AWS services, but it can also lead to increased
costs if not managed carefully. Use the AWS Pricing Calculator to model different scenarios and assess their financial impact.
Evaluate the total cost of ownership (TCO), which
includes both direct costs and indirect costs, such as the time and resources needed for
management and maintenance. Opting for managed services can reduce operational overhead,
but it might come at a higher price point.
Lastly, prioritize your security investments based on
risk assessment. Not all security services will be equally critical to your
infrastructure, so focus your budget on the areas that will have the most significant
impact on reducing risk and ensuring compliance. Balancing cost-effectiveness with the
level of security that you need is key to a successful AWS security strategy.
- Organizational structure and access needs
-
Evaluate how your organization is structured and operates, and how your access needs
might vary by team, project, or location. This factors in to how you manage and
authenticate user identities, assign roles, and enforce access controls across your AWS
environment. Implement best practices, such as the
applying least-privilege permissions and requiring multi-factor authentication (MFA).
Most organizations need a multi-account environment.
Review best practices for
this type of environment, and consider using AWS Organizations and AWS Control Tower to help you
implement it.
Another aspect that you should consider is the management of credentials and access keys. Consider using IAM Identity Center for centralizing access
management across multiple AWS accounts and business applications, which enhances both
security and user convenience. To help you smoothly manage access across your
organization's accounts, IAM Identity Center integrates with AWS Organizations.
Additionally, evaluate how these identity and access management services integrate with your existing directory services. If you have an
existing identity provider, you can integrate it with IAM Identity Center by using SAML
2.0 or OpenID Connect (OIDC).
IAM Identity Center also has support for System for Cross-domain
Identity Management (SCIM) provisioning to help keep your directories
synchronized. This helps you ensure a seamless and secure user experience while accessing
AWS resources.
Choose an AWS security, identity, and governance service
Now that you know the criteria for evaluating your security options, you're ready to choose
which AWS security services might be a good fit for your organizational requirements.
The following table highlights which services are optimized for which circumstances. Use the
table to help determine the service that is the best fit for your organization and use case.
1 Integrates with AWS Security Hub (full list)
2 Integrates with Amazon GuardDuty (full list)
3 Integrates with Amazon Security Lake (full list)
Choose AWS identity and access management services
Grant appropriate individuals the appropriate level of access to systems, applications,
and data.
| When should you use it?
|
What is it optimized for?
|
Security, identity, and governance services
|
| Use these services to help you securely manage and govern access for
your customers, workforce, and workloads. |
Helps you connect your source of identities, or create users. You can centrally
manage workforce access to multiple AWS accounts and applications. |
AWS IAM Identity Center
|
| Optimized for authenticating and authorizing users for web and mobile
applications. |
Amazon Cognito
|
| Optimized for securely sharing resources within AWS. |
AWS RAM
|
| Enables secure, fine-grained control over access to AWS workload resources. |
IAM
1
|
Choose AWS data protection services
Automate and simplify data protection and security tasks that range from key management
and sensitive data discovery to credential management.
| When should you use it?
|
What is it optimized for?
|
Data protection services
|
| Use these services to help you achieve and maintain the
confidentiality, integrity, and availability of sensitive data stored and processed
within AWS environments. |
Optimized for discovering sensitive data. |
Amazon Macie
1
|
| Optimized for cryptographic keys. |
AWS KMS
|
| Optimized for HSMs. |
AWS CloudHSM
|
| Optimized for private SSL/TLS X.509 certificates and keys. |
AWS Certificate Manager
|
| Optimized for creating private certificate authority hierarchies. |
AWS Private CA
|
| Optimized for database credentials, application credentials, OAuth tokens, API
keys, and other secrets. |
AWS Secrets Manager
|
| Optimized for providing access to cryptographic functions and key management used
in payment processing in accordance with PCI standards. |
AWS Payment Cryptography
|
Choose AWS network and application protection services
Centrally protect your internet resources against common DDoS and application attacks.
| When should you use it?
|
What is it optimized for?
|
Network and application protection services
|
| Use these services to help you enforce detailed security policies at
every network control point. |
Optimized for centrally configuring and managing firewall rules. |
AWS Firewall Manager
1
|
| Optimized for providing a stateful, managed network firewall and intrusion
detection and prevention service. |
AWS Network Firewall
|
| Optimized for protecting against DDoS attacks for AWS resources at the network,
transport, and application layers. |
AWS Shield
|
| Optimized for providing a web application firewall. |
AWS WAF
|
Choose AWS detection and response services
Continuously identify and prioritize security risks, while integrating security best
practices early.
| When should you use it?
|
What is it optimized for?
|
Detection and response services
|
| Use these services to help you detect and respond to security risks
across your
accounts, so you can protect your workloads at scale. |
Optimized for automating security checks and centralizing security alerts with
AWS and third-party integrations. |
AWS Security Hub
2, 3 |
| Optimized for assessing, auditing, and evaluating the configuration of your
resources. |
AWS Config
1
|
| Optimized for logging events from other AWS services as an audit trail. |
AWS CloudTrail
|
| Optimized for intelligent threat detection and detailed reporting. |
Amazon GuardDuty
1
|
| Optimized for vulnerability management. |
Amazon Inspector
1
|
| Optimized for centralizing security data. |
Amazon Security Lake
1
|
| Optimized for aggregating and summarizing potential security issues. |
Amazon Detective
1, 2, 3
|
| Optimized for helping you triage findings, escalate security events, and manage
cases that require your immediate attention. |
AWS Security Incident Response
|
Choose AWS governance and compliance services
Establish cloud governance across your resources, and automate your compliance and
auditing processes.
| When should you use it?
|
What is it optimized for?
|
Governance and compliance services
|
| Use these services to help you implement best practices and meet
industry standards when using AWS. |
Optimized for centrally managing multiple accounts and consolidated billing. |
AWS Organizations
|
| Optimized for providing on-demand downloads of AWS security and compliance
documents. |
AWS Artifact
|
| Optimized for auditing AWS usage. |
AWS Audit Manager
1 |
| Optimized for setting up and governing an AWS multi-account environment. |
AWS Control Tower
|
Use AWS security, identity, and governance services
You should now have a clear understanding of what each AWS security, identity, and
governance service (and the supporting AWS tools and services) does, and which ones might be
right for you.
To explore how to use and learn more about each of the available AWS security, identity,
and governance services, we have provided a pathway to explore how each of the services works.
The following sections provide links to in-depth documentation, hands-on tutorials, and
resources to get you started.
Use AWS identity and access management services
The following tables show some useful identity and access management resources, organized
by service, to help you get started.
- AWS IAM Identity Center
-
-
Enabling AWS IAM Identity Center
Enable IAM Identity Center and begin using it with your AWS Organizations.
Explore the
guide
-
Configure user access with the default IAM Identity Center
directory
Use the default directory as your identity source and set up and test user
access.
Get started
with the tutorial
-
Using Active Directory as an identity source
Complete the basic setup for using Active Directory as an IAM Identity Center identity
source.
Get
started with the tutorial
-
Configure SAML and SCIM with Okta and IAM Identity Center
Set up a SAML connection with Okta and IAM Identity Center.
Get started with the tutorial
- Amazon Cognito
-
-
Getting started with Amazon Cognito
Learn about the most common Amazon Cognito tasks.
Explore the
guide
-
Tutorial: Creating a user pool
Create a user pool, which allows your users to sign in to your web or
mobile app.
Get
started with the tutorial
-
Tutorial: Creating an identity pool
Create an identity pool, which allows your users to obtain temporary AWS
credentials to access AWS services.
Get started with the
tutorial
-
Amazon Cognito workshop
Practice using Amazon Cognito to build an authentication solution for a
hypothetical pet store.
Get started with the
tutorial
- AWS RAM
-
-
Getting started with AWS RAM
Learn about AWS RAM terms and concepts.
Explore the guide
-
Working with shared AWS resources
Share AWS resources that you own, and access AWS resources that are
shared with you.
Explore the guide
-
Managing permissions in AWS RAM
Learn about the two types of managed permissions: AWS managed
permissions and customer managed permissions.
Explore the
guide
-
Configure detailed access to your resources that are
shared using AWS RAM
Use customer managed permissions to customize your resource access and
achieve the best practice of least privilege.
Read the blog
- IAM
-
-
Getting started with IAM
Create IAM roles, users, and policies using the AWS Management Console.
Get started with the tutorial
-
Delegate access across AWS accounts using
roles
Use a role to delegate access to resources in different AWS accounts
that you own called Production and Development.
Get
started with the tutorial
-
Create a customer managed policy
Use the AWS Management Console to create a customer managed policy and then attach that policy to an IAM
user in your AWS account.
Get started with
the tutorial
-
Define permissions to access AWS resources based on
tags
Create and test a policy that allows IAM roles with principal tags to
access resources with matching tags.
Get
started with the tutorial
-
Security best practices in IAM
Help secure your AWS resources by using IAM best practices.
Explore the guide
Use AWS data protection services
The following section provides you with links to detailed resources that describe AWS
data protection.
- Macie
-
-
Getting started with Amazon Macie
Enable Macie for your AWS account, assess your Amazon S3 security posture,
and configure key settings and resources for discovering and reporting
sensitive data in your S3 buckets.
Explore the guide
-
Monitoring data security and privacy with
Amazon Macie
Use Amazon Macie to monitor Amazon S3 data security and assess your security
posture.
Explore
the guide
-
Analyzing Amazon Macie findings
Review, analyze, and manage Amazon Macie findings.
Explore the
guide
-
Retrieving sensitive data samples with Amazon Macie
findings
Use Amazon Macie to retrieve and reveal samples of sensitive data that are
reported by individual findings.
Explore the guide
-
Discovering sensitive data with Amazon Macie
Automate the discovery, logging, and reporting of sensitive data in your
Amazon S3 data estate.
Explore the guide
- AWS KMS
-
-
Getting started with AWS KMS
Manage symmetric encryption KMS keys, from creation to deletion.
Explore the
guide
-
Special-purpose keys
Learn about the different types of keys that AWS KMS supports, in addition
to symmetric encryption KMS keys.
Explore the guide
-
Scaling your encryption at rest capabilities with
AWS KMS
Learn about the encryption at rest options available within AWS.
Explore the workshop
- AWS CloudHSM
-
-
Getting started with AWS CloudHSM
Create, initialize, and activate an AWS CloudHSM cluster.
Explore the
guide
-
Managing AWS CloudHSM clusters
Connect to your AWS CloudHSM cluster and the various administrative tasks in
managing your cluster.
Explore the
guide
-
Managing HSM users and keys in AWS CloudHSM
Create users and keys on the HSMs in your cluster.
Explore the
guide
-
Automate the deployment of an NGINX web service using
Amazon ECS with TLS offload in CloudHSM
Use AWS CloudHSM to store your private keys for your websites that are hosted in
the cloud.
Read the blog
- AWS Certificate Manager
-
-
Requesting a public certificate
Use the AWS Certificate Manager (ACM) console or AWS CLI to request a public ACM
certificate.
Explore the
guide
-
Best practices for AWS Certificate Manager
Learn best practices based on real-world experience from current ACM
customers.
Explore the guide
-
How to use AWS Certificate Manager to enforce certificate issuance
controls
Use IAM condition keys to ensure that your users are issuing or
requesting TLS certificates in accordance with your organization's guidelines.
Read the blog
- AWS Private CA
-
-
Planning your AWS Private CA deployment
Prepare AWS Private CA for use before you create a private certificate authority.
Explore the guide
-
AWS Private CA administration
Create an entirely AWS hosted hierarchy of root and subordinate
certificate authorities for internal use by your organization.
Explore the
guide
-
Certificate administration
Perform basic certificate administration tasks with AWS Private CA, such as
issuing, retrieving, and listing private certificates.
Explore the guide
-
AWS Private CA workshop
Develop hands-on experience with various use cases of private certificate
authorities.
Explore the workshop
-
How to simplify certificate provisioning in Active
Directory with AWS Private CA
Use AWS Private CA to more easily provision certificates for users and machines
within your Microsoft Active Directory environment.
Read the blog
-
How to enforce DNS name constraints in
AWS Private CA
Apply DNS name constraints to a subordinate CA by using the AWS Private CA service.
Read the blog
- AWS Secrets Manager
-
-
AWS Secrets Manager concepts
Perform basic certificate administration tasks with AWS Private CA, such as
issuing, retrieving, and listing private certificates.
Explore the
guide
-
Set up alternating users rotation for
AWS Secrets Manager
Set up an alternating users rotation for a secret that contains database
credentials.
Explore the guide
-
Using AWS Secrets Manager secrets with Kubernetes
Show secrets from Secrets Manager as files mounted in Amazon EKS pods by using the
AWS Secrets and Configuration Provider (ASCP).
Explore the guide
- AWS Payment Cryptography
-
-
Getting started with AWS Payment Cryptography
Create keys and use them in various cryptographic operations.
Explore
the guide
-
AWS Payment Cryptography FAQs
Understand the basics of AWS Payment Cryptography.
Explore the FAQs
Use AWS network and application
protection services
The following tables provide links to detailed resources that describe AWS network and
application protection.
- AWS Firewall Manager
-
-
Getting started with AWS Firewall Manager policies
Use AWS Firewall Manager to activate different types of security policies.
Explore the
guide
-
How to continuously audit and limit security groups with
AWS Firewall Manager
Use AWS Firewall Manager to limit security groups, ensuring that only required ports
are open.
Read the blog
-
Use AWS Firewall Manager to deploy protection at scale in
AWS Organizations
Use AWS Firewall Manager to deploy and manage security policies across your AWS Organizations.
Read the blog
- AWS Network Firewall
-
-
Getting started with AWS Network Firewall
Configure and implement an AWS Network Firewall firewall for a VPC with a basic
internet gateway architecture.
Explore
the guide
-
AWS Network Firewall Workshop
Deploy an AWS Network Firewall by using infrastructure as code.
Explore the
workshop
-
Hands-on walkthrough of the AWS Network Firewall flexible
rules engine – Part 1
Deploy a demonstration of AWS Network Firewall within your AWS account to interact
with its rules engine.
Read the blog
-
Hands-on walkthrough of the AWS Network Firewall flexible
rules engine – Part 2
Create a firewall policy with a strict rule order and set one or more
default actions.
Read the blog
-
Deployment models for AWS Network Firewall
Learn deployment models for common use cases where you can add AWS Network Firewall
to the traffic path.
Read the blog
-
Deployment models for AWS Network Firewall with VPC routing
enhancements
Use enhanced VPC routing primitives to insert AWS Network Firewall between workloads
in different subnets of the same VPC.
Read the blog
- AWS Shield
-
-
How AWS Shield works
Learn how AWS Shield Standard and AWS Shield Advanced provide protections against DDoS
attacks for AWS resources at the network and transport layers (layer 3 and
4) and the application layer (layer 7).
Explore the guide
-
Getting started with AWS Shield Advanced
Get started with AWS Shield Advanced by using the Shield Advanced console.
Explore the
guide
-
AWS Shield Advanced workshop
Protect internet-exposed resources against DDoS attacks, monitor DDoS
attacks against your infrastructure, and notify the appropriate teams.
Explore the workshop
- AWS WAF
-
-
Getting started with AWS WAF
Set up AWS WAF, create a web ACL, and protect Amazon CloudFront by adding rules
and rules groups to filter web requests.
Get started with the
tutorial
-
Analyzing AWS WAF Logs in Amazon CloudWatch Logs
Set up native AWS WAF logging to Amazon CloudWatch logs and visualize and analyze
the data in the logs.
Read the blog
-
Visualize AWS WAF logs with an Amazon CloudWatch
dashboard
Use Amazon CloudWatch to monitor and analyze AWS WAF activity by using CloudWatch
metrics, Contributor Insights, and Logs Insights.
Read the blog
Use AWS detection and response services
The following tables provide links to detailed resources that describe AWS detection and
response services.
- AWS Config
-
-
Getting started with AWS Config
Set up AWS Config and work with AWS SDKs.
Explore the
guide
-
Risk and Compliance workshop
Automate controls by using AWS Config and AWS Managed Config Rules.
Explore the workshop
-
AWS Config Rule Development Kit library: Build and
operate rules at scale
Use the Rule Development Kit (RDK) to build a custom AWS Config rule and
deploy it with the RDKLib.
Read the blog
- AWS CloudTrail
-
- AWS Security Hub
-
Enabling AWS Security Hub
Enable AWS Security Hub with AWS Organizations or in a standalone account.
Explore the
guide
-
Cross-Region aggregation
Aggregate AWS Security Hub findings from multiple AWS Regions to a single
aggregation Region.
Explore the
guide
-
AWS Security Hub workshop
Learn how to use AWS Security Hub and to manage and improve the security posture
of your AWS environments.
Explore the
workshop
-
Three recurring Security Hub usage patterns and how to
deploy them
Learn about the three most common AWS Security Hub usage patterns and how to
improve your strategy for identifying and managing findings.
Read the blog
- Amazon GuardDuty
-
-
Getting started with Amazon GuardDuty
Enable Amazon GuardDuty, generate sample findings, and set up alerts.
Explore the tutorial
-
EKS protection in Amazon GuardDuty
Use Amazon GuardDuty to monitor your Amazon Elastic Kubernetes Service (Amazon EKS) audit logs.
Explore the
guide
-
Lambda protection in Amazon GuardDuty
Identify potential security threats when you invoke an AWS Lambda function.
Explore the guide
-
GuardDuty Amazon RDS protection
Use Amazon GuardDuty to analyze and profile Amazon Relational Database Service (Amazon RDS) login activity for
potential access threats to your Amazon Aurora databases.
Explore the guide
-
Amazon S3 protection in Amazon GuardDuty
Use GuardDuty to monitor CloudTrail data events and to identify potential
security risks within your S3 buckets.
Explore the guide
-
Threat detection and response with Amazon GuardDuty and
Amazon Detective
Learn the basics of Amazon GuardDuty and Amazon Detective.
Explore the
workshop
- Amazon Inspector
-
Getting started with Amazon Inspector
Activate Amazon Inspector scans to understand findings in the console.
Get started with
the tutorial
-
Vulnerability management with Amazon Inspector
Use Amazon Inspector to scan Amazon EC2 instances and container images in Amazon Elastic Container Registry
(Amazon ECR) for software vulnerabilities.
Explore the
workshop
-
How to scan EC2 AMIs by using Amazon Inspector
Build a solution by using multiple AWS services to scan your AMIs for
known vulnerabilities.
Read the blog
- Amazon Security Lake
-
-
Getting started with Amazon Security Lake
Enable and start using Amazon Security Lake.
Explore the guide
-
Managing multiple accounts with AWS Organizations
Collect security logs and events from multiple AWS accounts.
Explore the guide
-
Ingest, transform, and deliver events that are
published by Amazon Security Lake to Amazon OpenSearch Service
Ingest, transform, and deliver Amazon Security Lake data to Amazon OpenSearch Service for use by
your SecOps teams.
Read the blog
-
How to visualize Amazon Security Lake findings with
QuickSight
Query and visualize data from Amazon Security Lake by using Amazon Athena and QuickSight.
Read the blog
- Amazon Detective
-
-
Amazon Detective terms and
concepts
Learn the key terms and concepts that are important for
understanding Amazon Detective and how it works.
Explore the guide
-
Setting up Amazon Detective
Enable Amazon Detective from the Amazon Detective console,
Amazon Detective API, or AWS CLI.
Explore the guide
-
Threat detection and response with Amazon GuardDuty and
Amazon Detective
Learn the basics of Amazon GuardDuty and Amazon Detective.
Explore the
workshop
Use AWS governance and compliance services
The following tables provide links to detailed resources that describe governance and
compliance.
- AWS Organizations
-
-
Creating and configuring an organization
Create your organization and configure it with two AWS member accounts.
Get started
with the tutorial
-
Services that work with AWS Organizations
Understand which AWS services you can use with AWS Organizations and the
benefits of using each service on an organization-wide level.
Explore the guide
-
Organizing your AWS environment by using multiple
accounts
Implement best practices and current recommendations for organizing your
overall AWS environment.
Read the whitepaper
- AWS Artifact
-
-
Getting started with AWS Artifact
Download security and compliance reports, manage legal agreements, and
manage notifications.
Explore the guide
-
Managing agreements in AWS Artifact
Use the AWS Management Console to review, accept, and manage agreements for your
account or organization.
Explore the guide
-
Prepare for an Audit in AWS Part 1 – AWS Audit
Manager, AWS Config, and AWS Artifact
Use AWS services to help you automate the collection of evidence that's
used in audits.
Read the blog
- AWS Audit Manager
-
Enabling AWS Audit Manager
Enable Audit Manager by using the AWS Management Console, the Audit Manager API, or the AWS CLI.
Explore the
guide
-
Tutorial for Audit Owners: Creating an
assessment
Create an assessment by using the Audit Manager Sample Framework.
Explore
the guide
-
Tutorial for Delegates: Reviewing a
control set
Review a control set that was shared with you by an audit owner
in Audit Manager.
Explore the guide
- AWS Control Tower
-
-
Getting started with AWS Control Tower
Set up and launch a multi-account environment, called a landing zone, that
follows prescriptive best practices.
Explore the guide
-
Modernizing Account Management with Amazon Bedrock
and AWS Control Tower
Provision a security tooling account and leverage generative AI to
expedite the AWS account setup and management process.
Read the blog
-
Building a well-architected AWS GovCloud (US)
environment with AWS Control Tower
Set up your governance in the AWS GovCloud (US) Regions, including
governing your AWS workloads by using Organizational Units (OUs) and
AWS accounts.
Read the blog
Explore AWS security, identity, and governance services
- Editable architecture diagrams
-
Reference
architecture diagrams
Explore reference architecture diagrams to help you develop your security,
identity, and governance strategy.
Explore security, identity, and governance reference architectures
- Ready-to-use code
-
- Documentation
-